How to Prevent Data Breaches in Your Business?
Data breaches in businesses are a serious issue that can have far-reaching impacts on both the company and society. Once a breach occurs, the business may face the following dilemmas:
- Leakage of Trade Secrets: A company's data often contains a large amount of trade secrets, such as product design, research and development progress, marketing strategies, etc. If this information is leaked, it may be exploited by competitors, thereby severely affecting the company's competitive position.
- Legal Liability: Many countries and regions have strict data protection regulations, such as the General Data Protection Regulation (GDPR) in the European Union and China's Cybersecurity Law, etc. A company's data breach may violate these regulations, leading to significant fines and other serious legal consequences.
- Loss of Reputation: Data breach incidents usually cause serious damage to a company's reputation. Consumers may lose confidence in the company's data protection capabilities and choose other service providers.
As the scale of a business continues to expand, the number of people accessing the database also increases exponentially, and internal security issues will correspondingly increase. These issues may come from employees with weak security awareness, or employees who actively leak data due to dissatisfaction with the company, malicious revenge, bribery for personal gain, and other reasons.
NineData's SQL development standards (such as limiting the number of rows returned per query, the complexity of queries, etc.) can already prevent these phenomena to a certain extent, but currently, it only targets single query behavior. Users can obtain a large amount of data through continuous multiple queries. At this time, it is particularly important to limit the user's query behavior per day.
In the latest iteration, NineData has added a user access management feature for users under the organizational model. This feature helps you accurately control the number of SQL queries and the total number of rows that each user in the organization can query per day, further reducing the risk of corporate data breaches.
For information on how to use the organizational model, please refer to the previous article "Build a Corporate Database Security Access Platform with NineData in Three Minutes, Say Goodbye to Data Breaches and Database Deletion".
What can User Access Management do?
- Configure access volume based on user responsibilities: According to the responsibilities and work needs of users, configure the appropriate access volume for each user. For example, data analysts may need to frequently query a large amount of data, so their access volume may be higher than other users. In this way, it can be ensured that each user has sufficient permissions to complete their work.
- Flexibly adjust access volume for special circumstances: In some special circumstances, it may be necessary to temporarily increase or decrease the access volume of users. At this time, you can adjust the access volume of specific users individually.
- Batch configure access volume for all users in a department: According to the responsibilities and work needs of the department (organization), batch configure the appropriate access volume for all users in that department.
- Configure access volume for specific users individually and set an expiration time: In some cases, it may be necessary to temporarily increase or decrease the access volume of specific users. For example, if a user needs to perform a large-scale data query task, you can temporarily increase the access volume and set an expiration time. Once this time is reached, the user's access volume will automatically return to the normal level.
When is it necessary to configure user access volume?
The user access management feature can be applied to various scenarios, and the following are some common use cases:
- Data Security: Scenarios where companies need to prevent data breaches. For example, companies may need to prevent malicious users from stealing data through a large number of queries, or prevent internal employees from abusing their access permissions.
- Legal Compliance: For companies that need to comply with data protection regulations (such as GDPR or Cybersecurity Law), user access management is a key tool for achieving compliance. By restricting user access permissions and query times, companies can ensure that their database operations meet regulatory requirements.
- Emergency Response: In the face of cyber attacks or other security incidents, user access management can serve as an effective emergency response tool. For example, if it is detected that an account of a user may have been hacked, the access volume of that user can be immediately restricted to prevent data theft.
Demonstration of Effects
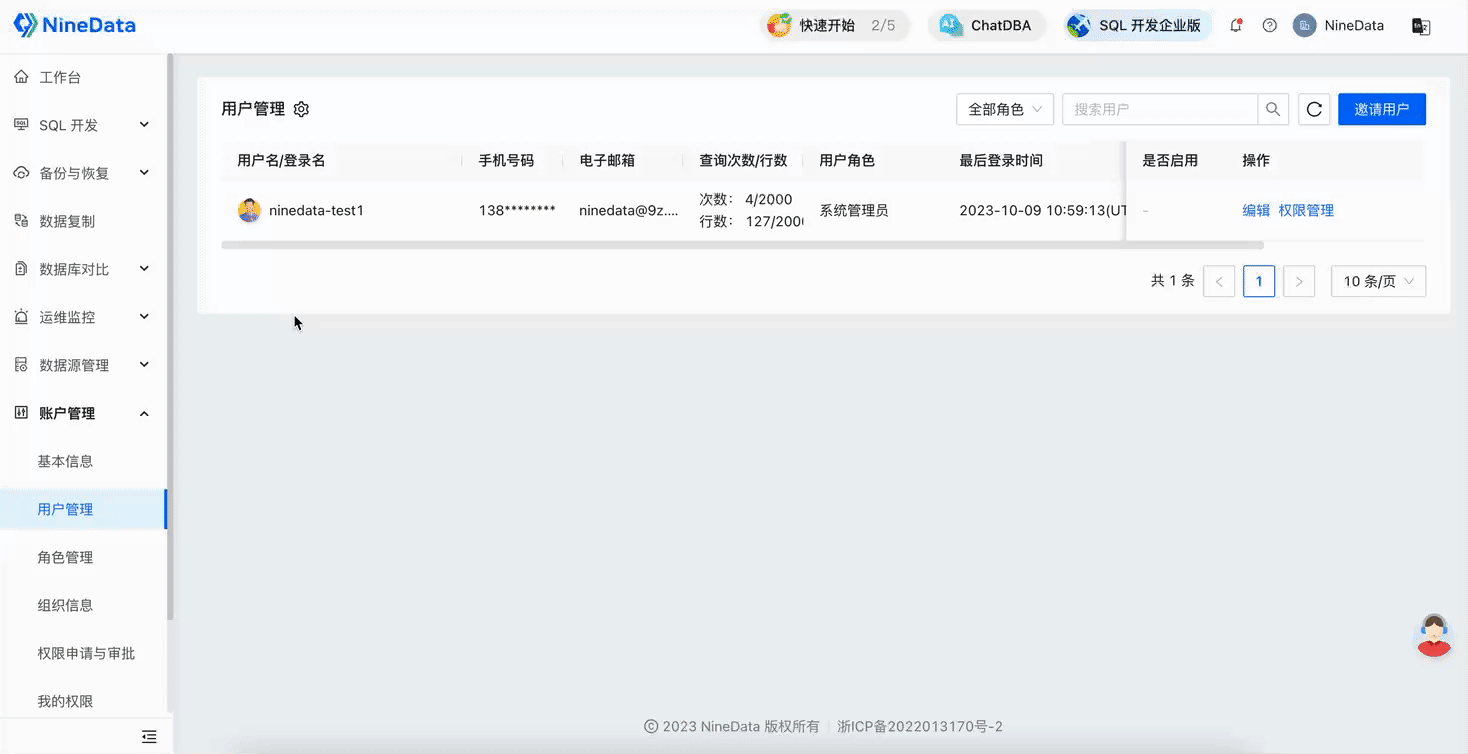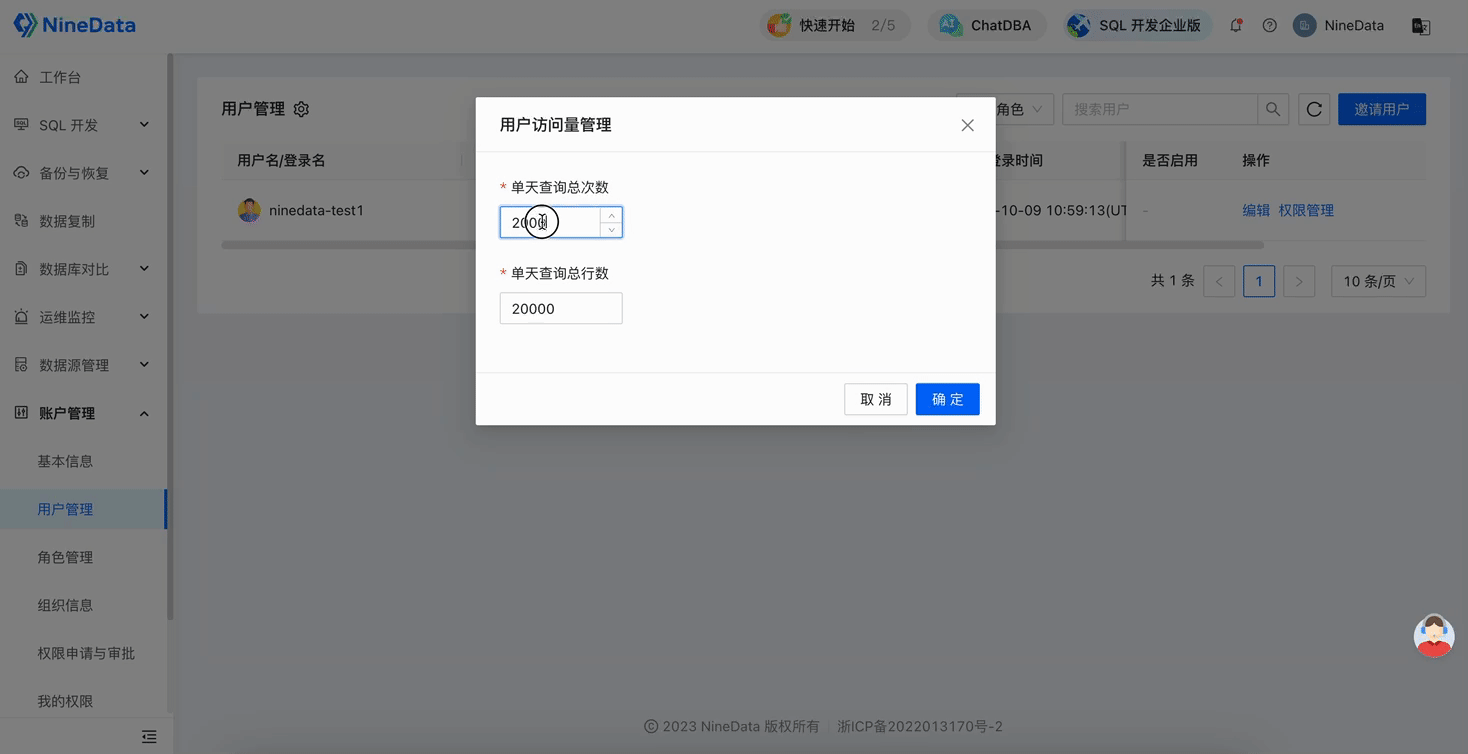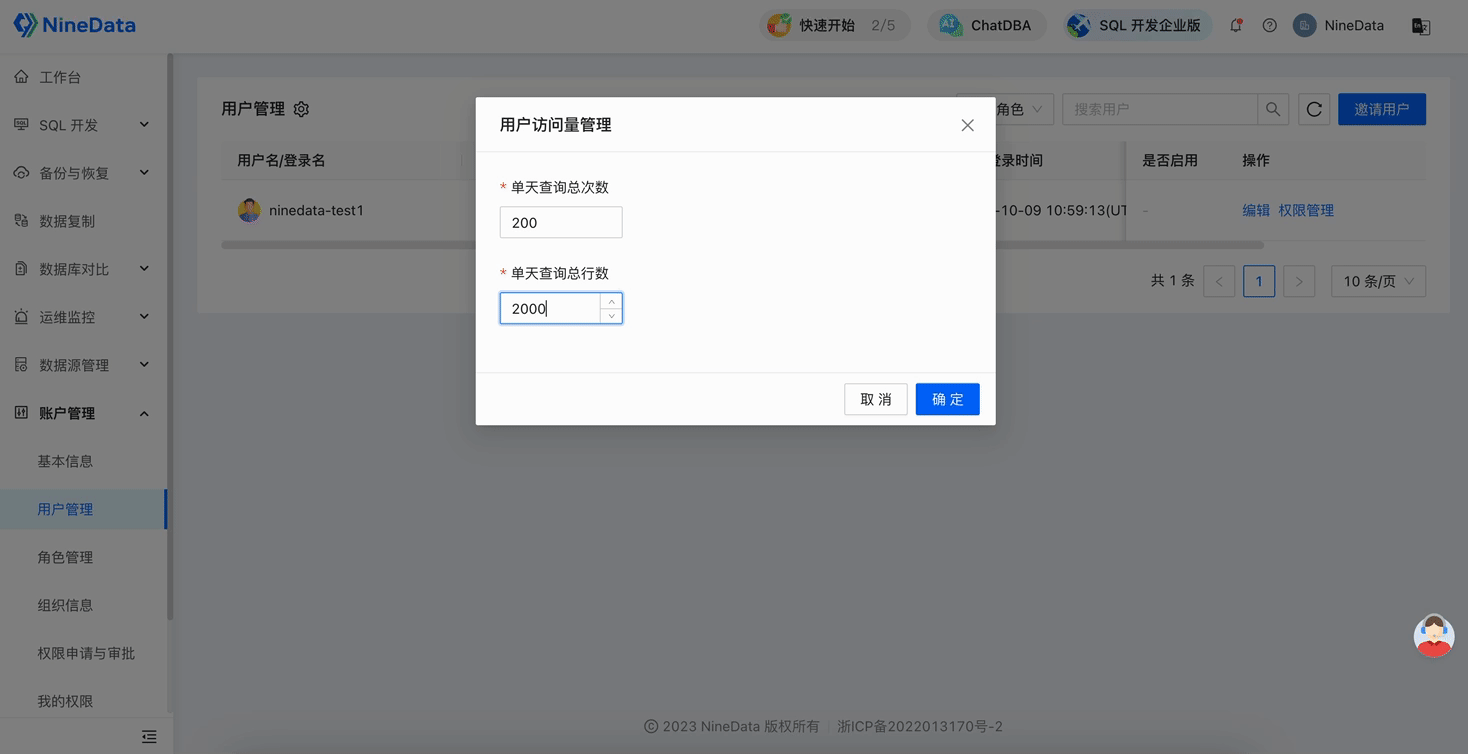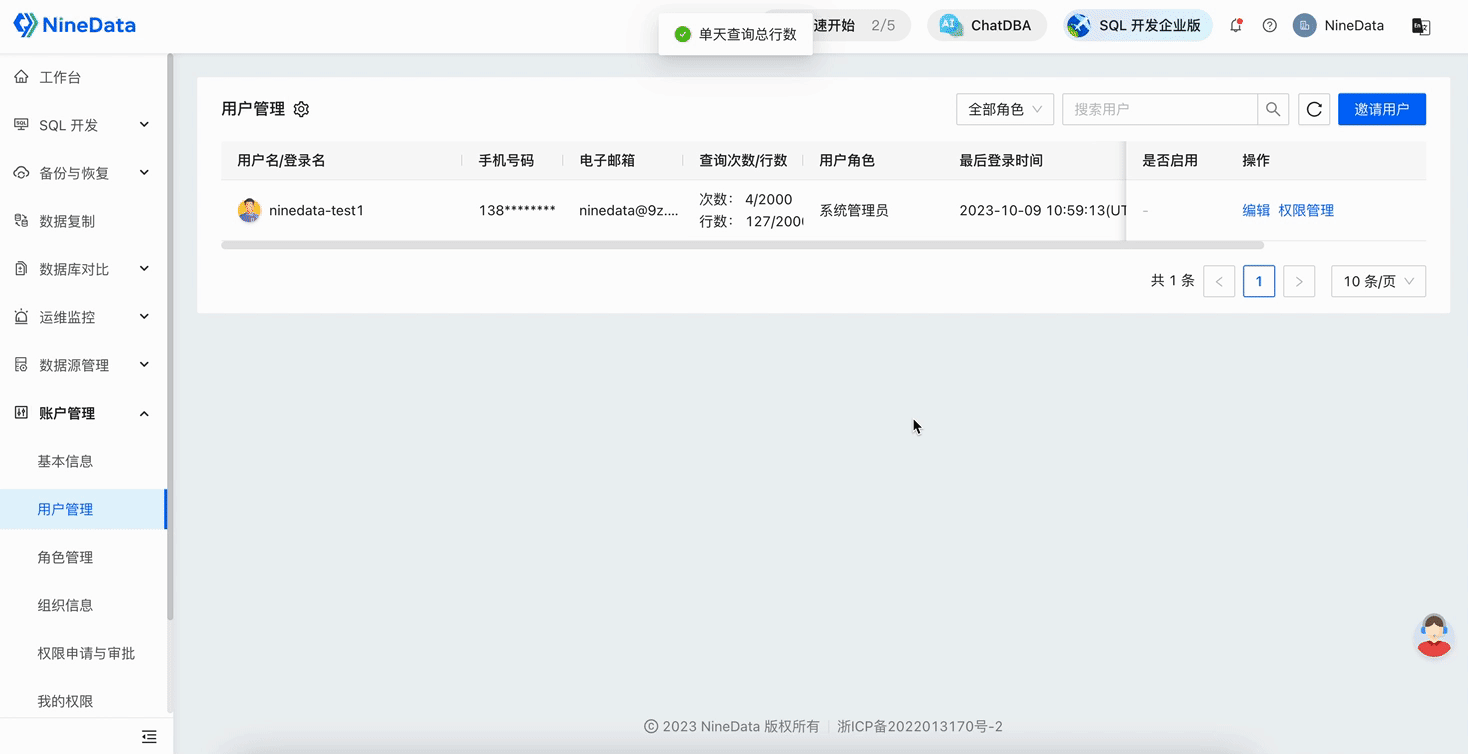
Query the number of queries executed by the user on the current day and the total number of query rows
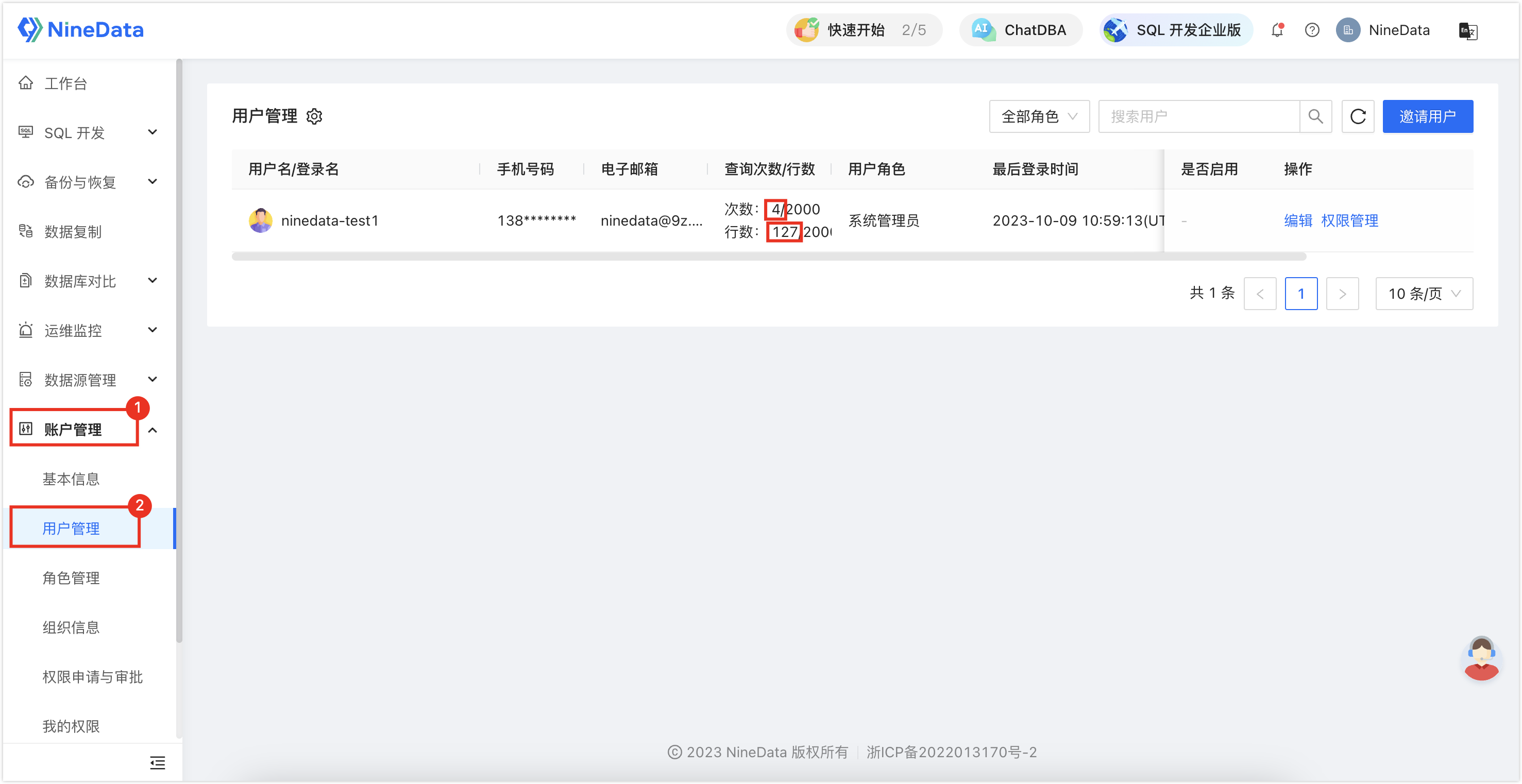
The number on the left is the used quota, and the number on the right is the available quota.
Configure query limits for the number of queries and the total number of query rows for global users
This configuration method is effective for all users within the organization. If you have configured the query limits for the number of queries and the total number of query rows for the target user individually, the individual configuration will take precedence over the global configuration.
Configure query limits for the number of queries and the total number of query rows for the target user

The query limits for the number of queries and the total number of query rows configured for the target user only take effect for that user, and the priority is higher than the global configuration.
Query effect after exceeding the limit

The system prompts that the query limit for the day has been exceeded, and the query is intercepted by the system.