Introduction to account management
NineData provides multi-person collaboration capabilities, which can be enabled after creating or joining an organization. This article introduces concepts such as organizations, users, roles, etc.
Organization
Under normal circumstances, after you register for a NineData account, the system automatically creates an organization with the same name for you and switches to that organization by default. You can manually switch to personal mode, which is suitable for individual developers. For example, it allows you to perform tasks such as backing up, restoring, synchronizing, and comparing your own databases, as well as collaborating with SQL Console for daily development work.
However, for enterprise users, there is a need for collaborative development among multiple individuals. In this scenario, various roles are responsible for different business aspects, necessitating different permissions to meet data security requirements. NineData provides an organization mode that supports assigning different roles and resource management permissions to each user within the organization. This mode is suitable for collaborative development among multiple users within the same organization, ensuring data security while enhancing overall productivity.
You can hover your mouse over the icon in the top right corner of the page to view the current mode you are in.
Personal Mode (SQL Dev. Personal)
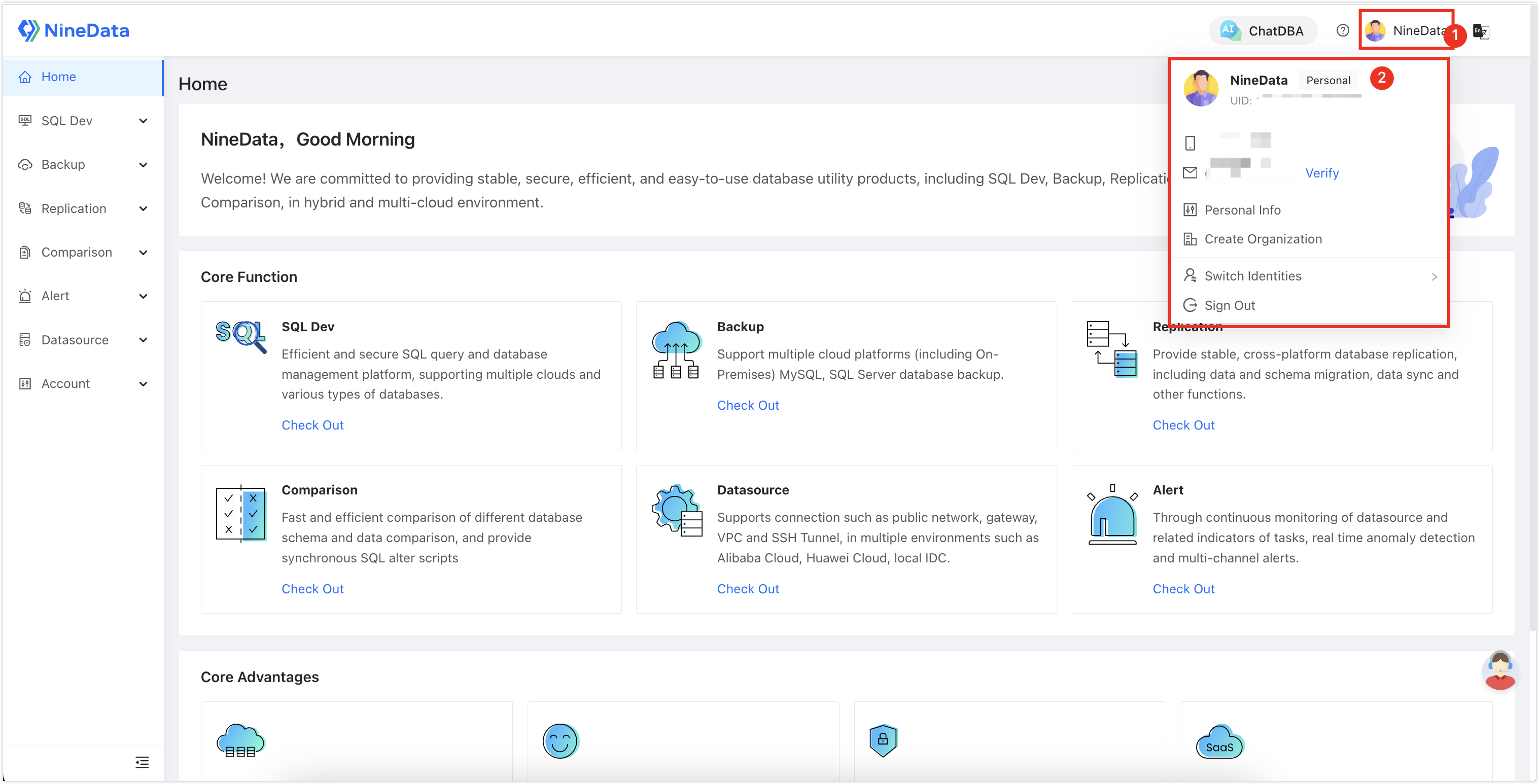
Organization Mode (DevOps Pro, DevOps Enterprise)
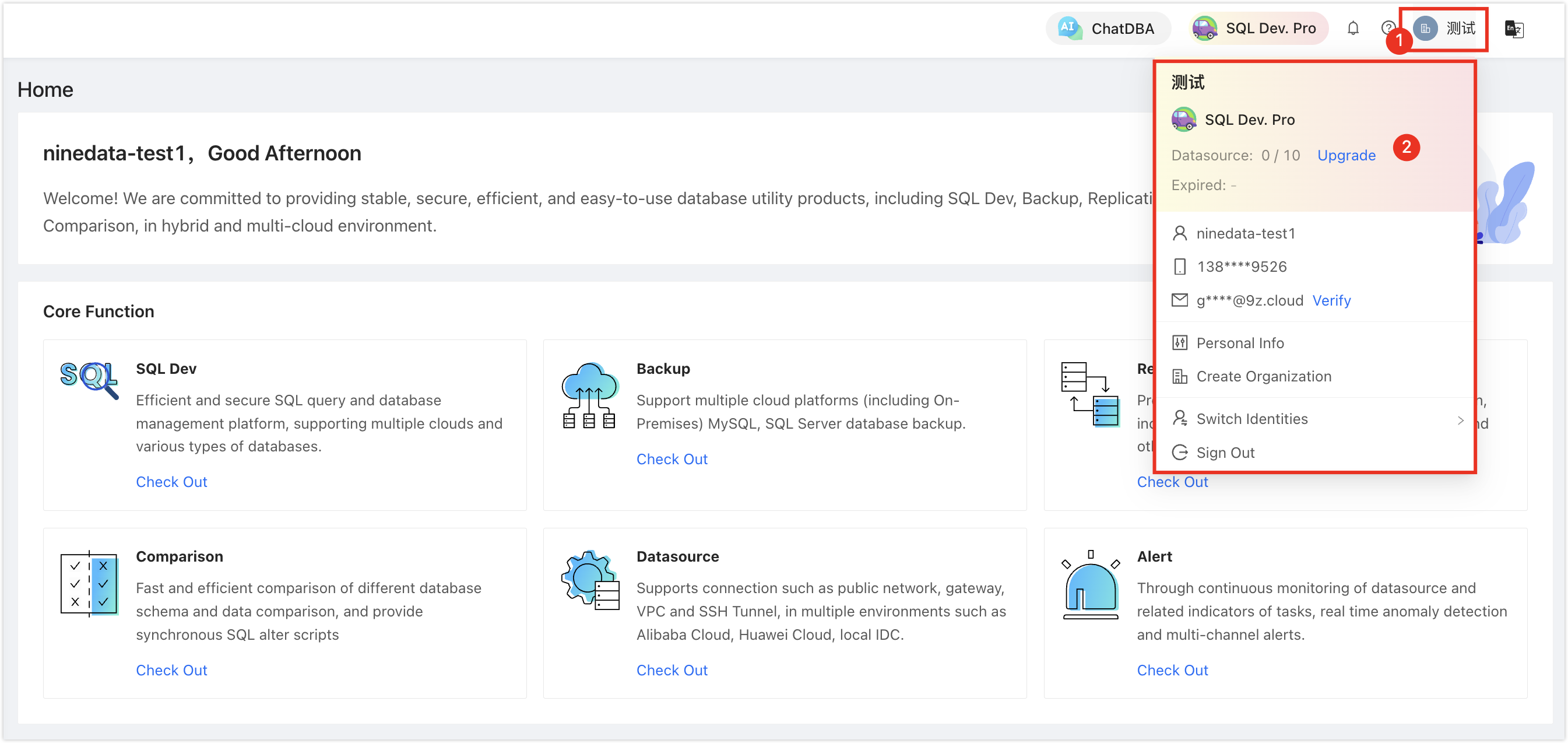
How to manage organizations, see Manage Organizations .
User
A user is an independent individual in NineData. In the personal mode, the user is oneself and has all the rights to resources. In organizational mode, a user is part of an organization, and the system administrator decides what role the user is and assigns corresponding resource permissions.
To figure out current mode, the user can place mouse over the icon in the upper right corner of the page, and mode information will pop out.
For more information about users, see Manage Users .
Role
The role determines the user's permission over resources. NineData provides the following 5 preset roles:
- System administrator: The user who creates the organization is the system administrator by default, and has all the permissions of the data sources in the organization; has the management rights of users and roles in the organization; has the permissions of all function modules.
- Production environment administrator: By default, has all the permissions of production environment data sources and function modules.
- Production environment read-only: By default, has read-only permissions for production environment data sources, as well as all function module permissions.
- Development environment administrator: By default, has all permissions for the development environment data sources and function modules.
- Ordinary members: have all functional module permissions.
- System administrators can delete and edit all preset roles except system administrators , and can add custom roles. For more information, see Managing Roles.
- For detailed permissions corresponding to each preset role, see Appendix: List of preset role permissions.
Permissions
There are four types of permissions in NineData:
Admin permissions: Manage users and roles within the current organization. Only Administrator has this permission.
Service Permission: Determines whether a user can see the six major modules on the left side of the console: DevOps, Backup, Replication, Comparison, Datasource, and Alert. The granularity is subdivided into sub-functional entrances within each module, such as SQL Console in the DevOps module.
Datasource Permission: Determines whether a user can perform operations such as editing, SQL querying, backup and recovery, data replication, and database comparison on the target data source.
tipDatasource Permission needs to be used in conjunction with Service Permission. For example, if a user has the permission to replicate data from a data source, but does not have the permission to replicate data in the module, they will still be unable to use the data replication feature.
Other Permission: Includes two permissions: Alert Permission and Sensitive Data Management.
- Alert Permission: Has the permission to configure alerts. For more information, see Managing Alerts.
- Sensitive Data Management: Has the permission to configure sensitive data sources. For more information, see Managing Sensitive Data.