How Does Your Personal Sensitive Information Leak?
You must have experienced various harassment calls, real estate agents, credit card centers, loans, etc. While you are fed up with hanging up these calls, have you ever thought about a question: where do these harassment calls come from?
For example, the famous Marriott Hotel had a data leak incident in 2018 involving up to 383 million guests, including sensitive information such as names, phone numbers, email addresses, passport numbers, check-in and check-out times, and even extremely sensitive content like credit card information. After the news was announced, Marriott International's stock price plummeted, and it was heavily fined £99 million by the UK Information Commissioner's Office (ICO) for violating the EU GDPR. The matter was not over yet. In 2020, Marriott experienced another data leak involving 5.2 million guests, and this time, it was through the login credentials of two employees at a Marriott franchised hotel. In the end, Marriott Hotel suffered a "Waterloo" in reputation.
Do you think this example is unrelated to the theme of this article? In fact, it is not. In addition to the personal information we "willingly" disclose when participating in various social activities, the most likely possibility is that major companies "leak" it for us. Imagine the various apps on your phone; when we register and use applications, personal information flows into the company's database. This is inevitable and not the problem. So, why does the data leak?
Why Does Data Leak?
When companies manage user data, whether they have sufficient security measures to protect the security of user data is the key point. In recent years, various leakage channels such as "insiders," "hacker attacks," and "third-party supply chains" have emerged endlessly. Taking Marriott as an example again, although Marriott has a privacy protection policy, in reality, many employees can easily access guests' sensitive information (see the data leak method of Marriott in 2020), and this is the root of the problem.
Speaking of this, we have to mention the topic of "compliance." Europe's General Data Protection Regulation (GDPR) and China's Personal Information Protection Law (PIPL) have put forward strict requirements for data protection. As the main holders and processors of data, companies have a huge responsibility. Even so, many companies lack awareness of data compliance and fail to encrypt, classify, and audit sensitive data as required, ultimately leading to data leaks. For companies, the consequences of a data leak can be devastating, with huge fines, lawsuits, and loss of brand reputation just the beginning. More importantly, the destruction of customer trust is irreparable.
China issued the national standard "Data Security Technology Data Classification and Grading Rules" on March 15, 2024, which clearly stipulates that data needs to be classified based on factors such as nature, source, and use, and risk levels are divided based on the impact of data on organizations, individuals, society, or the country. This rule will take effect on October 1, 2024. Through this clear classification and grading method, companies can better take appropriate protection measures for different types of data, reducing the risk of data leaks.
How to Classify and Grade the Management of Sensitive Corporate Data?
Corporate databases usually involve a large number of personnel management and operations. To prevent data leaks, effective classification and grading management is the foundation. Different types of data need to be graded according to their sensitivity and risk. Sensitive data at each level is managed by different responsible persons for permission control. For example, if an employee of a company needs to access a customer's name and phone number for a reasonable request, the sensitivity levels of the name and phone number are S3 and S4, respectively. Then the employee needs to apply for permissions for these two sensitive columns to the persons in charge of S3 and S4, maximizing the control of data access permissions, and there will be a trace if something goes wrong.
Through NineData's sensitive data protection function, this can be easily achieved. NineData comes with six sensitivity levels, S0 to S5, and corresponding identification rules, which can automatically identify sensitive data in the corporate database and desensitize it. Unauthorized users trying to access sensitive columns will only see desensitized data.
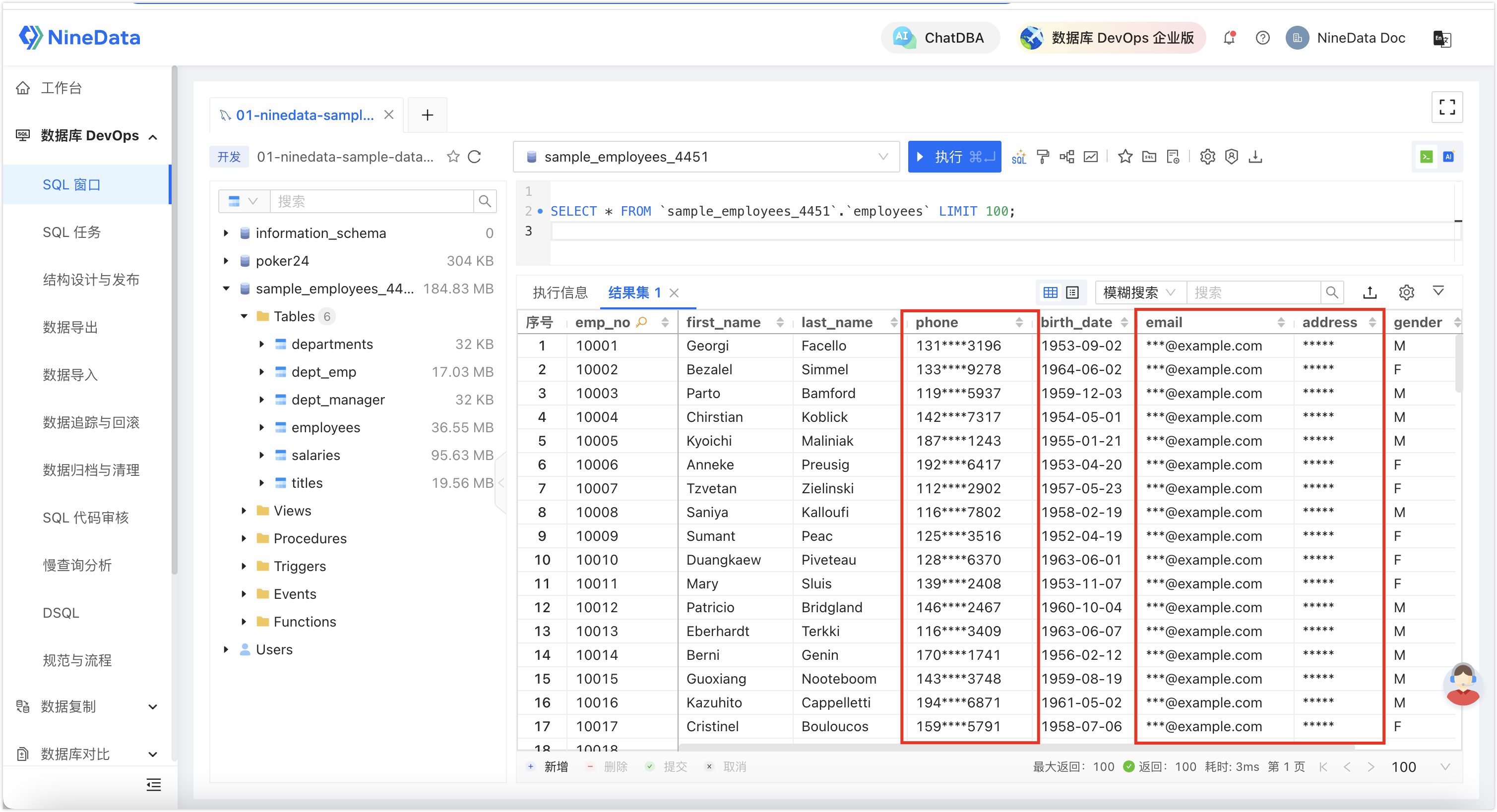
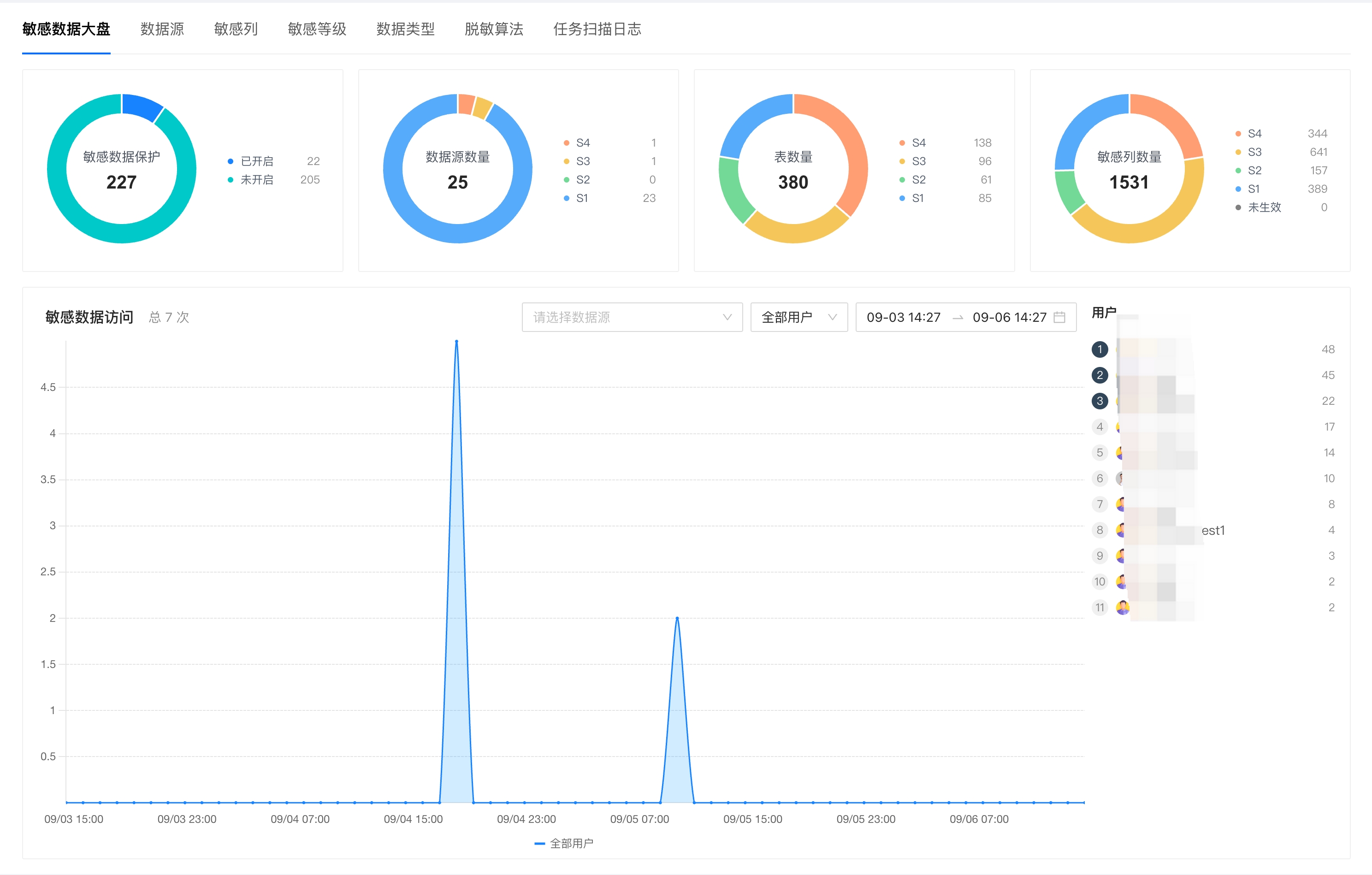
In addition, NineData's Sensitive Data Dashboard function displays information related to sensitive data under the current organization, including the total number of data sources supporting sensitive data protection, the total number of data sources with sensitive data enabled, sensitivity levels, the total number of tables with sensitive data enabled, the total number of sensitive columns, and the total number of sensitive data access times. Administrators can easily understand the overall situation of sensitive data in the corporate database.
Demonstration in Practice
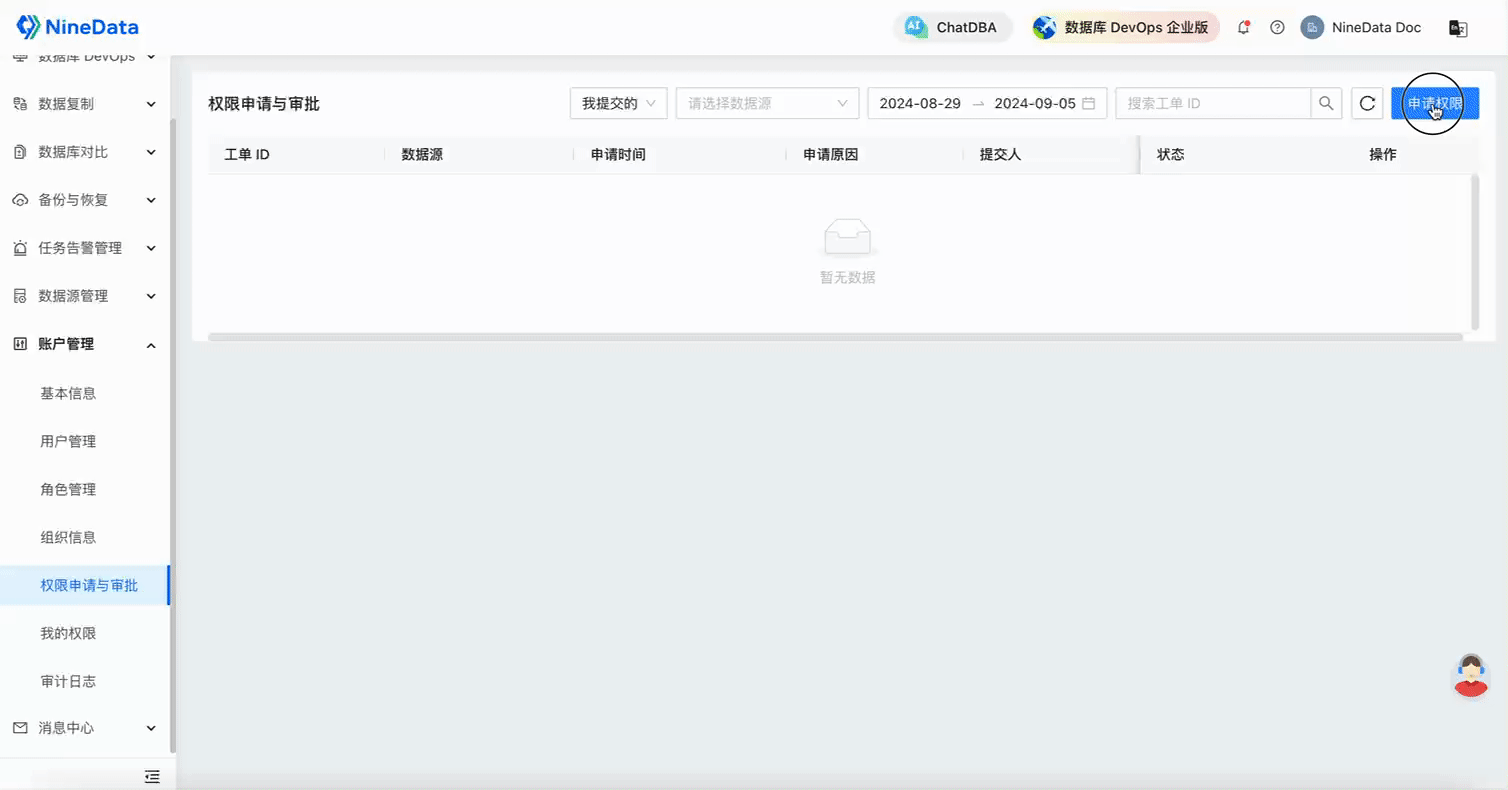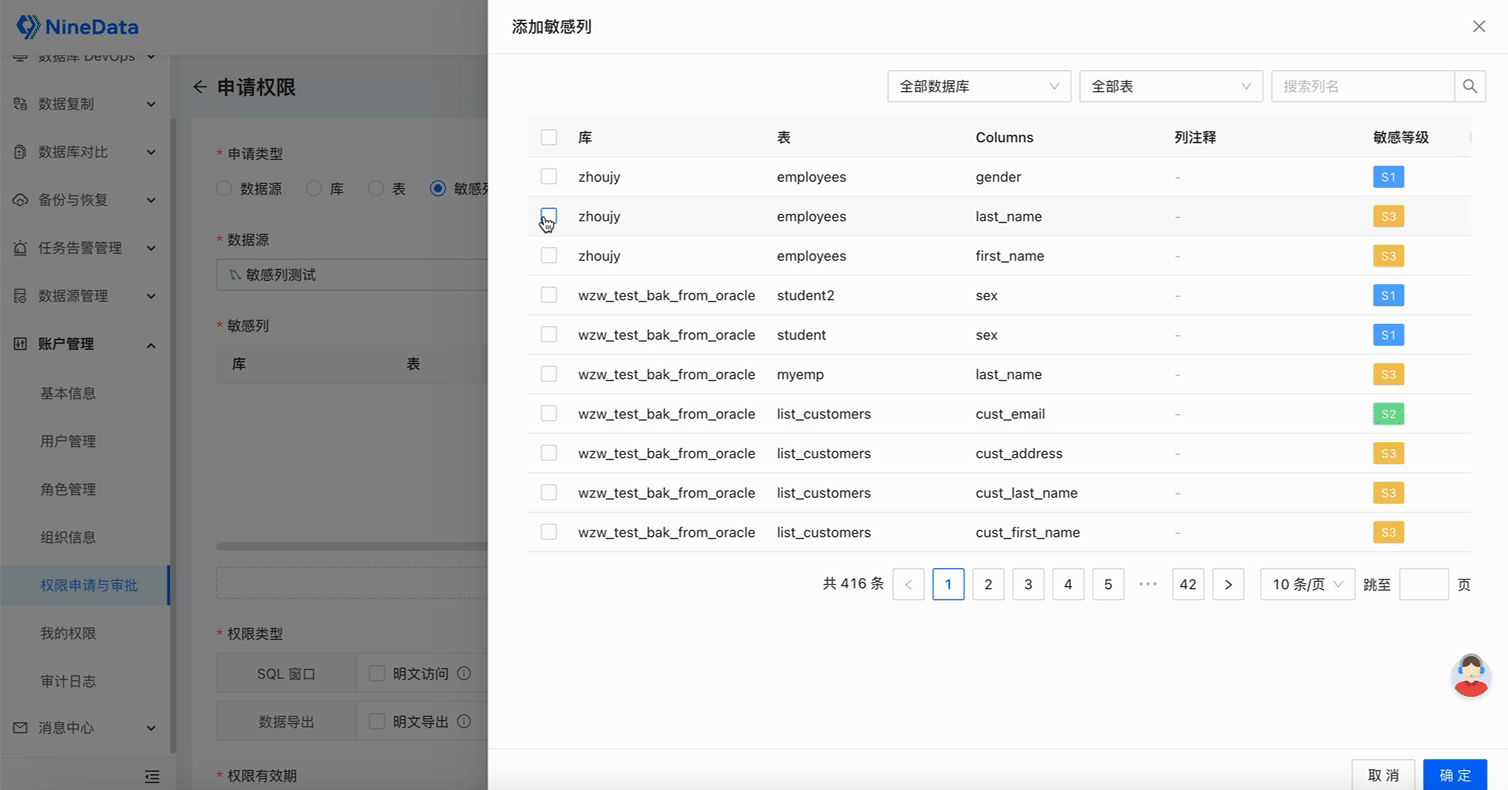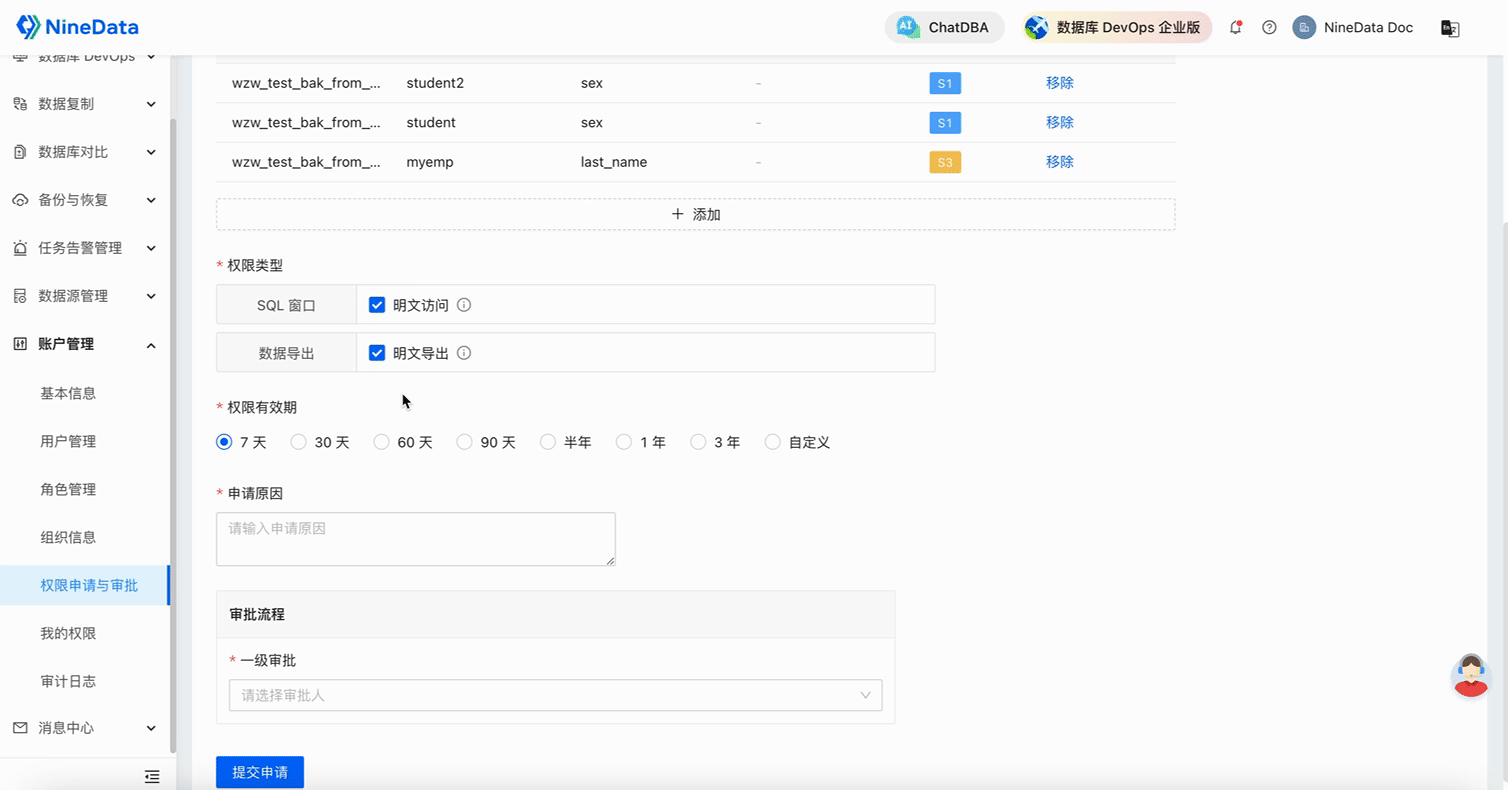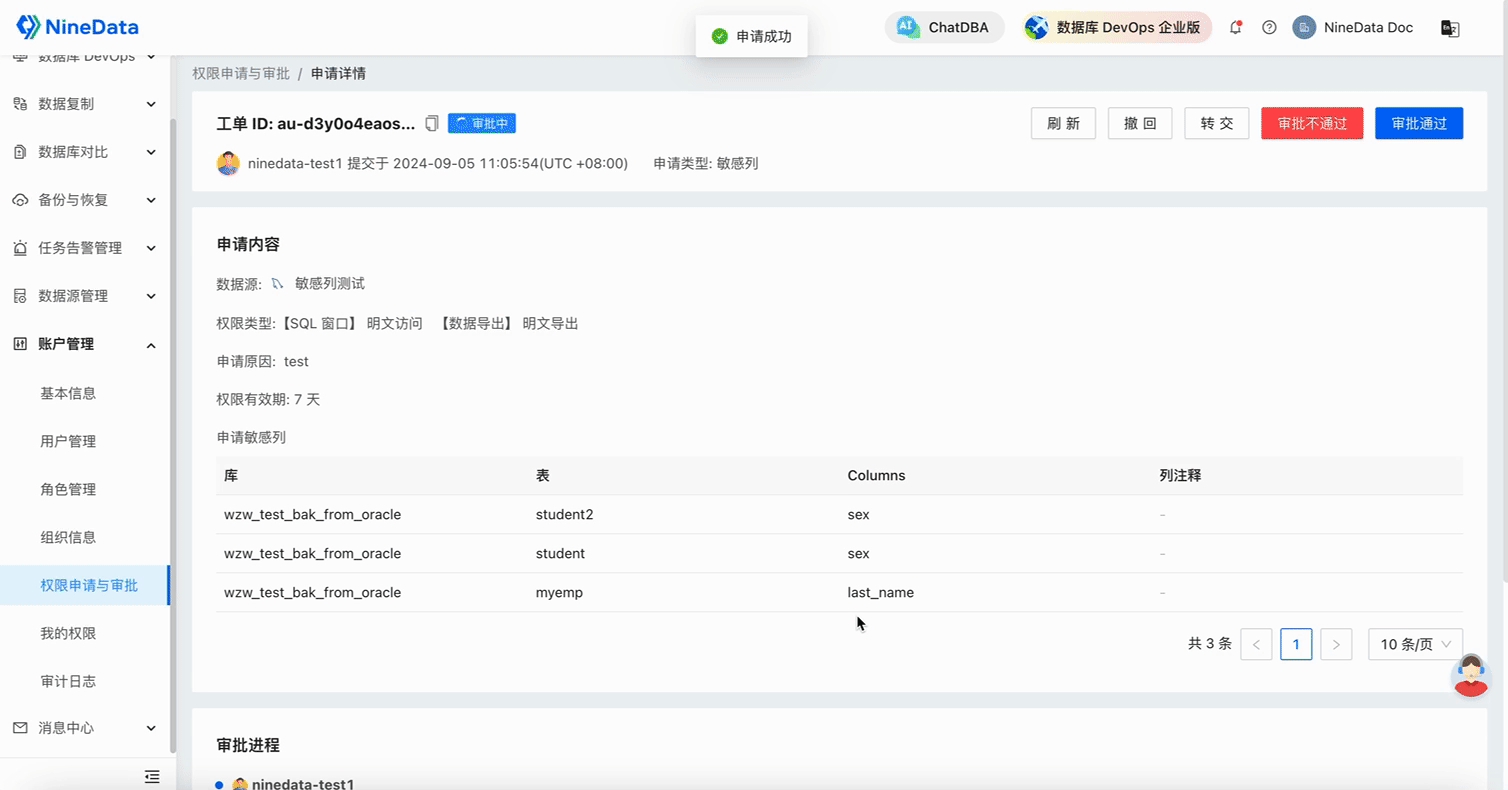
Add Sensitive Columns: Open the Sensitive Data Protection switch for the target data source, click Scan Settings in the Operation column, and click OK. If there is sensitive data in the table, it will automatically complete the addition of sensitive columns in a short time.
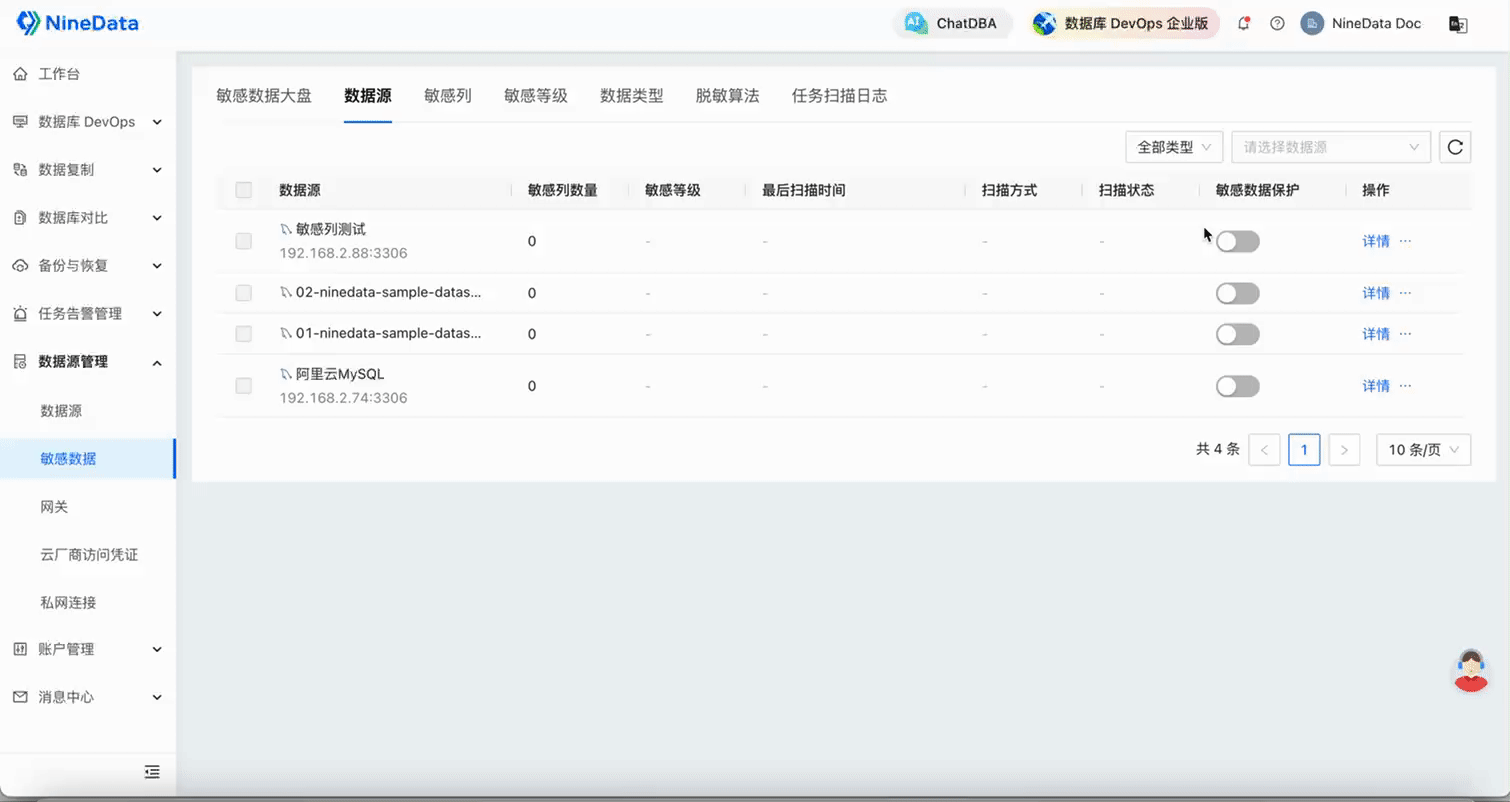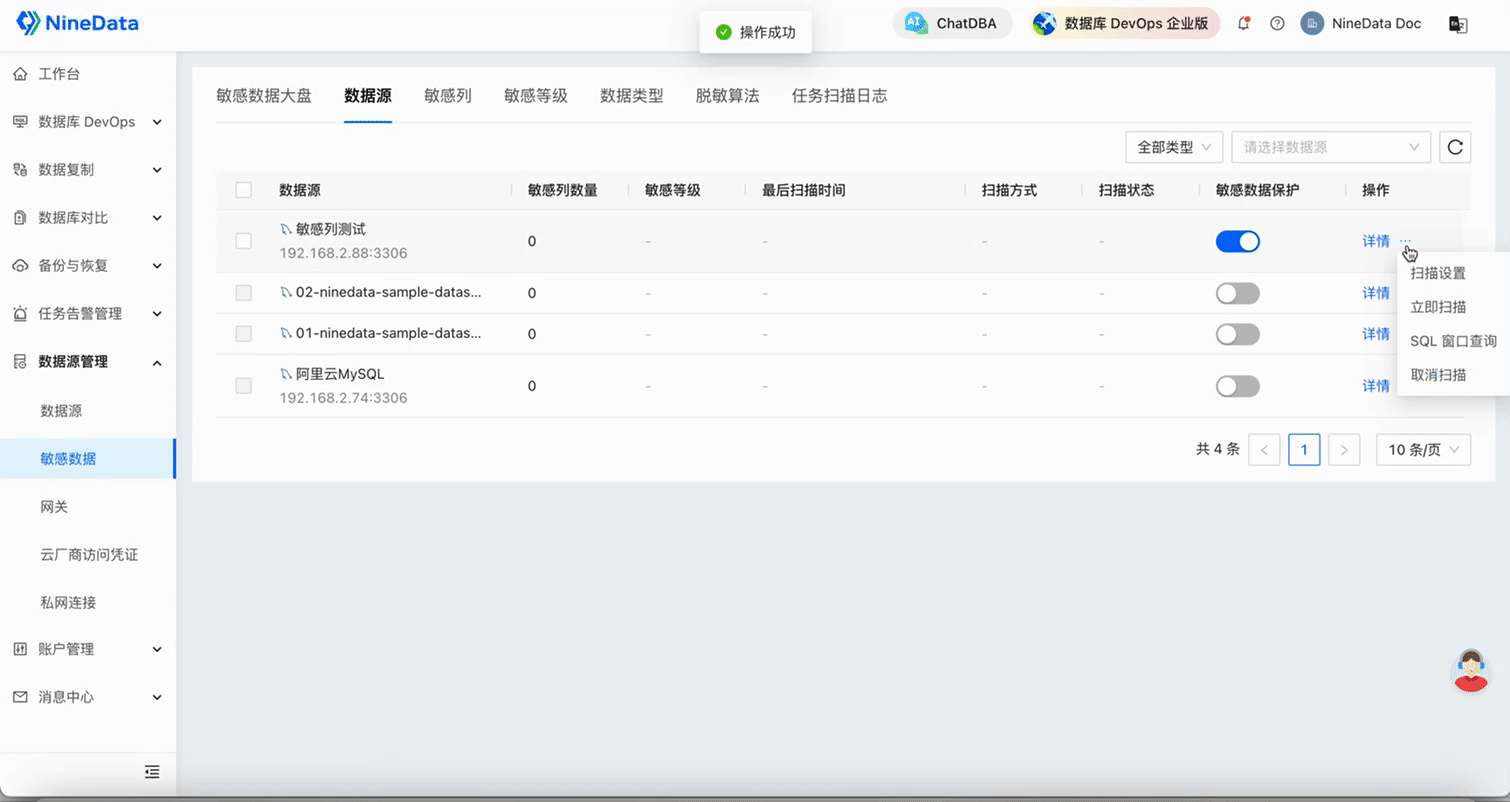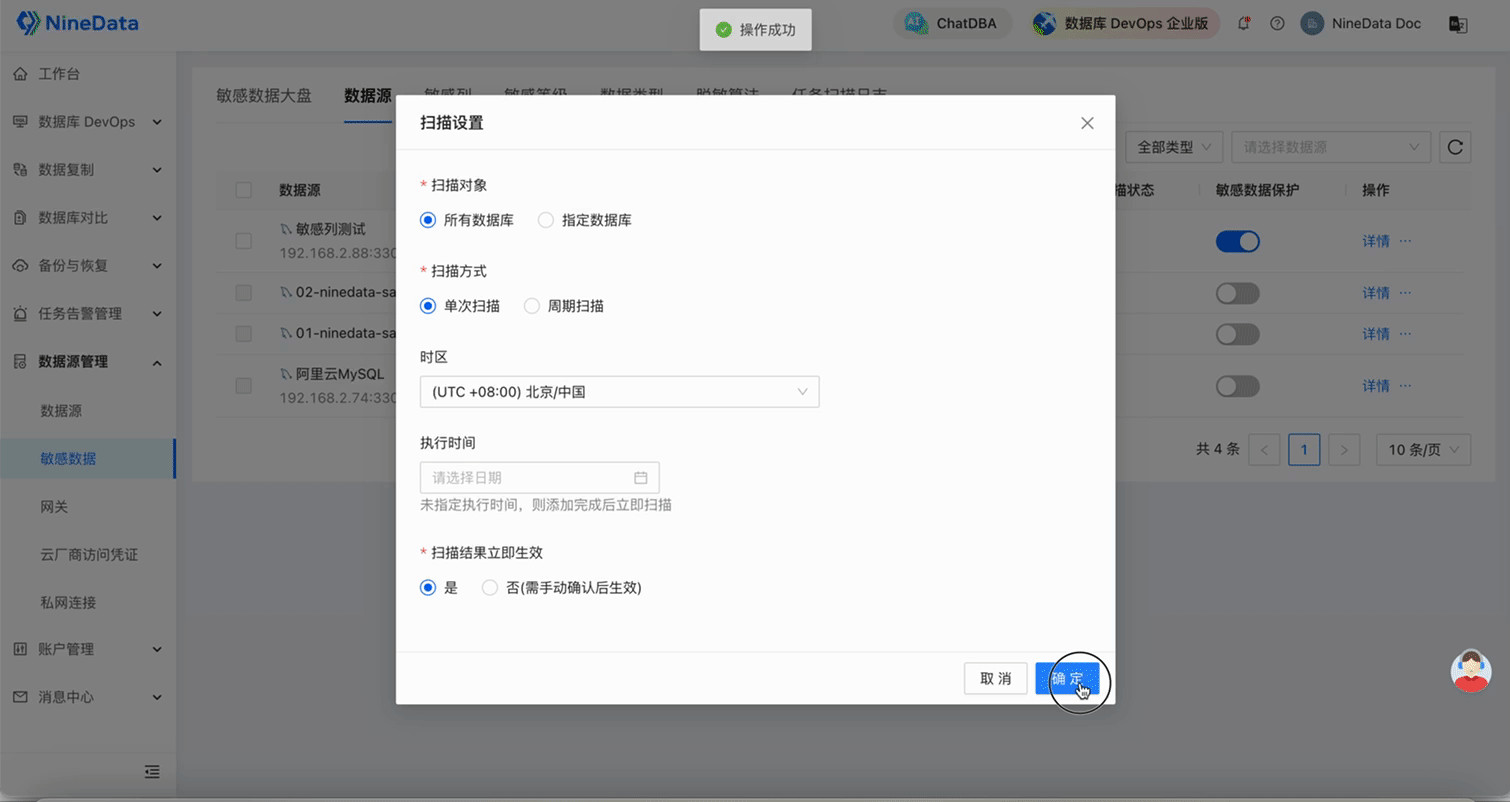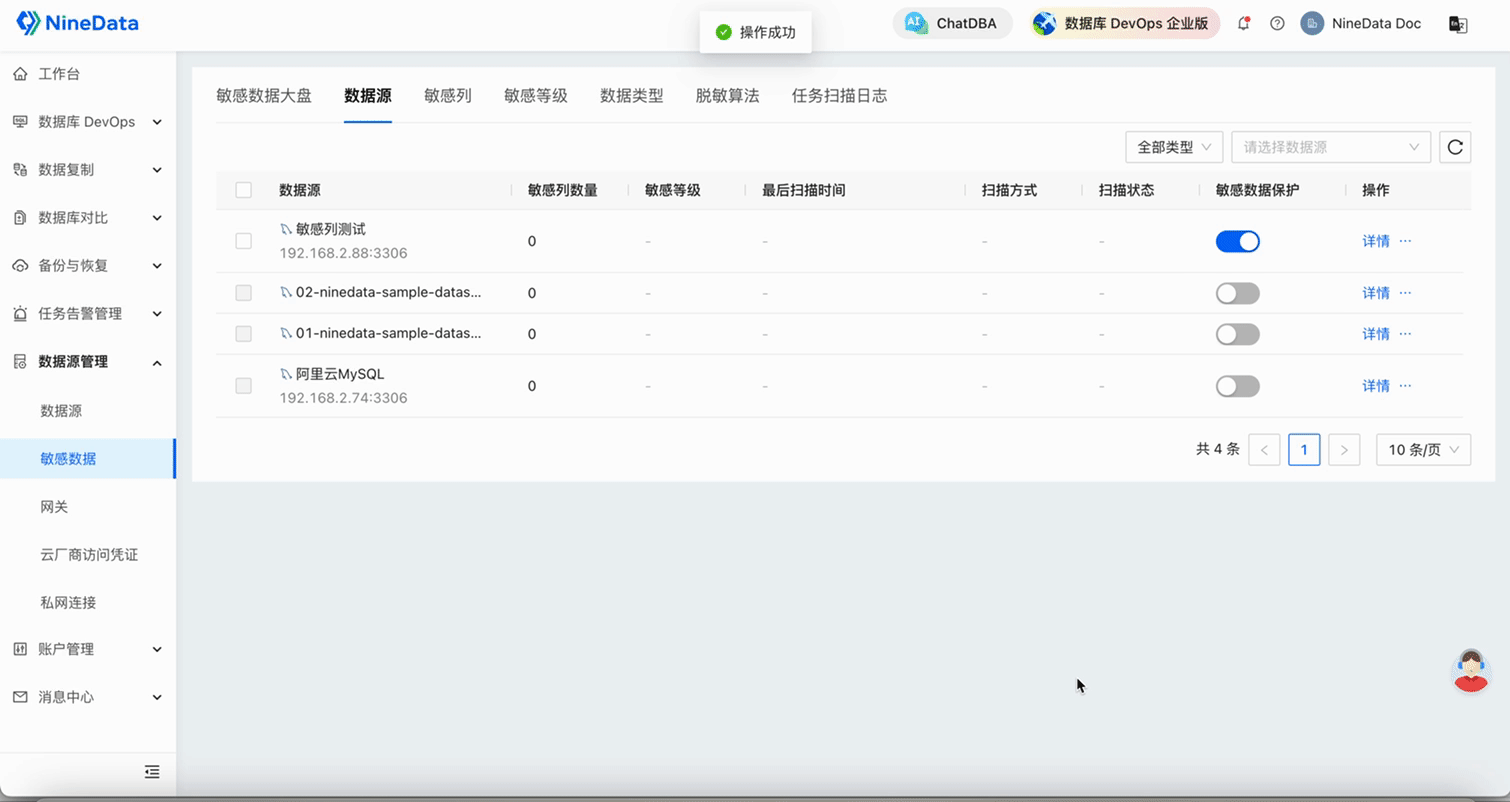
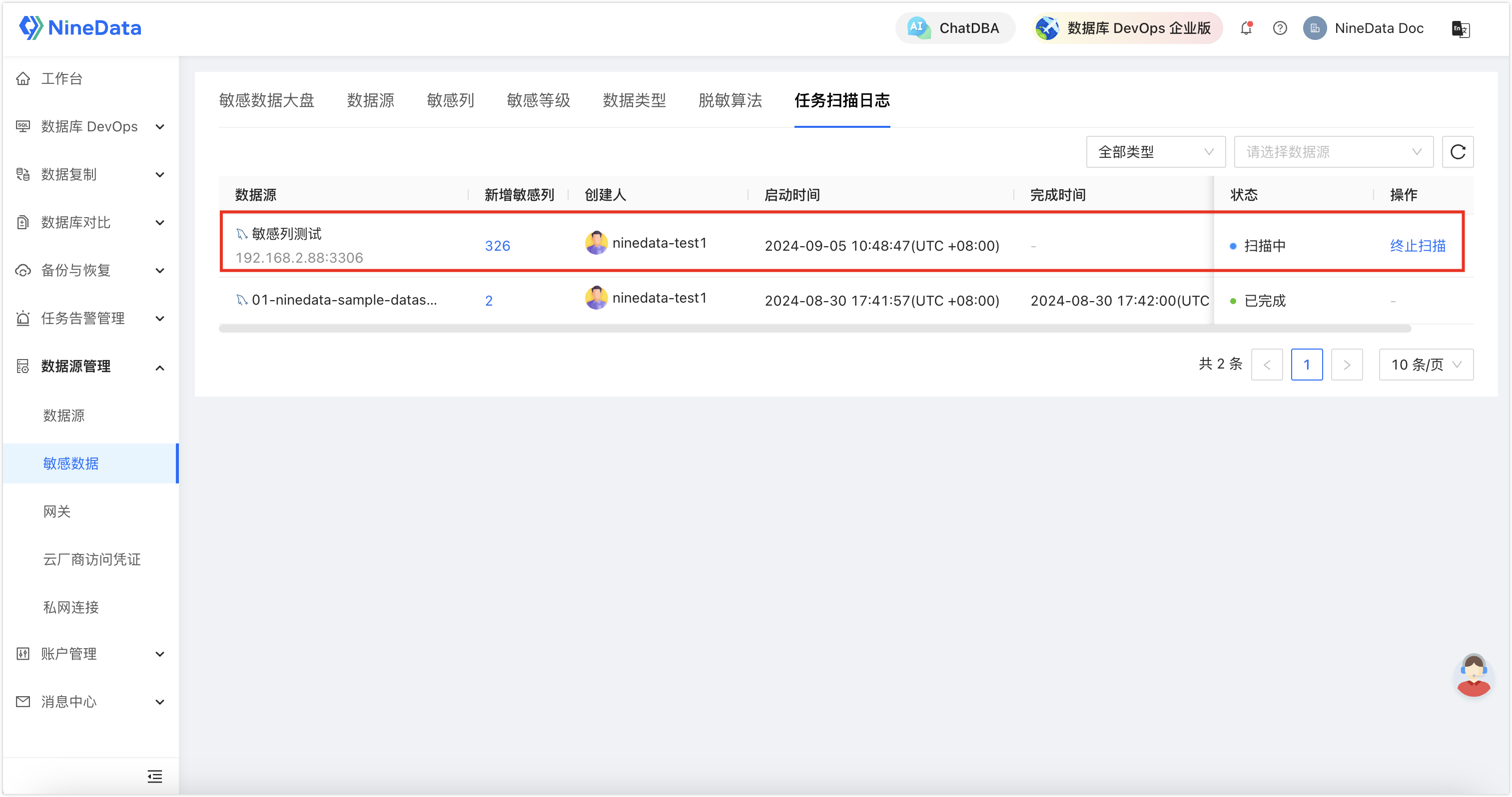
Yes, you're right, it's actually done. If your table is larger, the scan of sensitive columns will take a few minutes. At this time, you can check the scan status in the Task Scan Log.
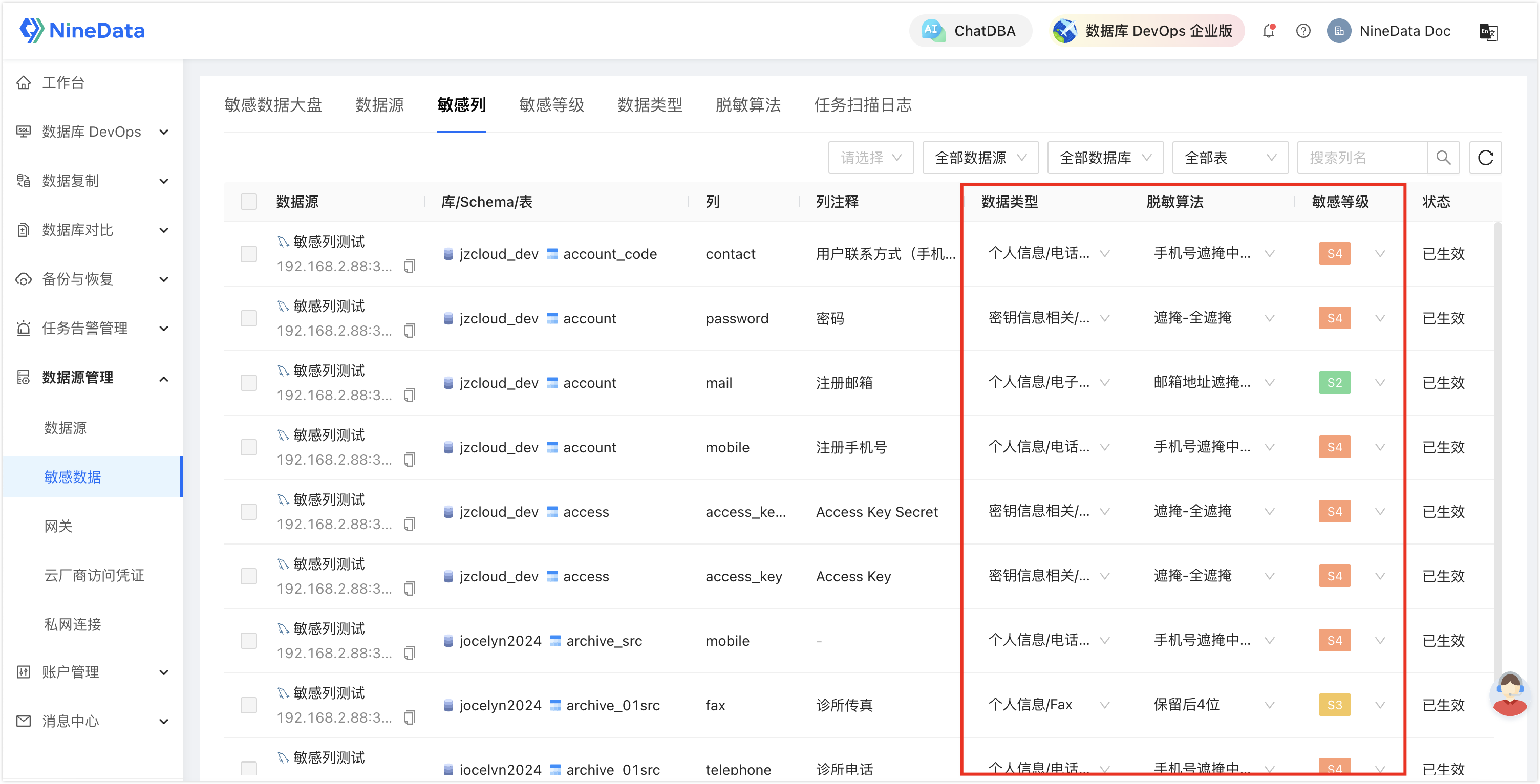
View Sensitive Columns: In the Sensitive Columns tab, you can view the scanned sensitive columns, and the content in the red box can be edited manually.
Configure the Approval Process for Sensitive Columns: Configure the approvers for sensitivity levels S1 to S5, making the database more secure and compliant.
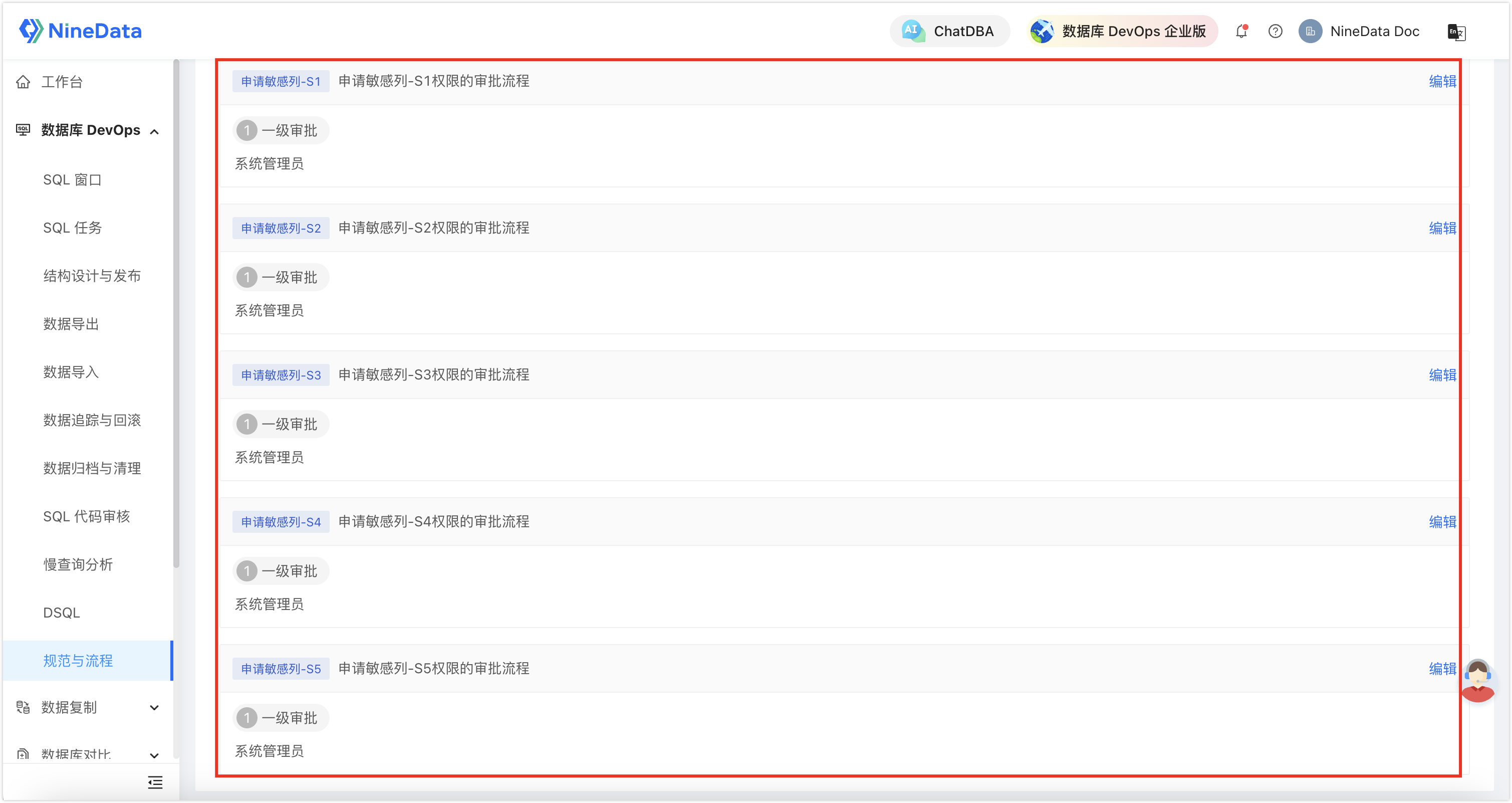
All configurations are now complete. When users access the database, if they involve access to sensitive columns, they need to apply for the corresponding permissions; otherwise, they cannot view the content of the sensitive columns.
Finally
To achieve the most standardized classification and grading of sensitive data, after seeing the above operation demonstration, do you think it's not so difficult? Preventing data leaks, corporate awareness is the most important, and the earlier the better, because you never know when the data leak problem will find you.