Integrating OpenLDAP with NineData SSO
This article is aimed at enterprises that manage personnel account information using OpenLDAP, providing a best practice guide for integrating OpenLDAP with Single Sign-On (SSO) to achieve unified authentication and authorization management. By integrating OpenLDAP, phpLDAPadmin, and Keycloak, you can easily log in to NineData through the SSO feature.
Background Information
OpenLDAP (Open Lightweight Directory Access Protocol) is an open-source Lightweight Directory Access Protocol (LDAP) server used for storing and managing organizational user accounts and identity information, widely used in enterprises. In most enterprises, there are multiple application systems running in parallel, and these application systems usually have independent identity authentication and authorization mechanisms, causing users to log in and manage accounts separately for each system. After integrating OpenLDAP with SSO, users can seamlessly access other systems with just one login, which not only simplifies the convenience brought by account management and system login processes but also reduces the risk of account information leakage and improves the overall security of the system.
Prerequisites
- You have already created or joined an organization, and the organization has subscribed to DevOps Enterprise. Please ensure that your annual or monthly subscription is still active. For more information, please refer to Manage Organizations.
- Your current account has been switched to the target organization. For more information, please refer to Switching to an Organization.
- Have Root privileges for the LDAP server, you can switch to the Root account by executing the
sudo sucommand before performing the steps in this article.
Environment Description
This article introduces the installation and configuration methods of all required software tools from 0 to 1, you can ignore the operation steps of the software that already exists in your system while reading. The environment description used in this article is as follows:
System version: CentOS Linux release 7.9.2009
tipYou can view the current system version by executing the
cat /etc/*releasecommand in the command line.Docker version: 24.0.0
Docker Compose version: 2.17.3
OpenLDAP version: 2.4.57
phpLDAPadmin version: 1.2.5
KeyCloak version: 9.0.0
Step One: Install Docker and Docker Compose
For easy installation and configuration, this article uses Docker and Docker Compose to run OpenLDAP, OpenLDAPAdmin, and KeyCloak.
The following are the installation steps using the yum command in Linux systems based on RPM package management such as CentOS or Red Hat Enterprise Linux (RHEL).
Click to expand process description
- Install Docker
- Install Docker Compose
Open the terminal command line tool and execute the following command to uninstall the old version of Docker (if any):
sudo yum remove docker docker-client docker-client-latest docker-common docker-latest docker-latest-logrotate docker-logrotate docker-engineInstall the yum package manager extension tool yum-utils:
sudo yum install -y yum-utilsSet up the Docker stable repository:
sudo yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repoInstall the latest version of Docker:
sudo yum install docker-ce docker-ce-cli containerd.ioStart the Docker service:
sudo systemctl start dockerVerify whether Docker is installed successfully:
sudo docker run hello-worldtipIf the following content is output in the command line, it means Docker has been successfully installed:
Hello from Docker! This message shows that your installation appears to be working correctly. ...
Open the terminal command line tool and execute the following command to download the Docker Compose binary content and save it to the docker-compose file in the /usr/local/bin/ directory.
curl -SL https://github.com/docker/compose/releases/download/v2.17.3/docker-compose-linux-x86_64 -o /usr/local/bin/docker-composeSet executable permissions for the docker-compose file.
sudo chmod u+x /usr/local/bin/docker-composeCreate a soft link for docker-compose to enable direct execution in any directory.
sudo ln -s /usr/local/bin/docker-compose /usr/bin/docker-composeVerify whether Docker Compose is installed successfully:
docker-composetipIf the following content is output in the command line, it means Docker Compose has been installed successfully:
Usage: docker compose [OPTIONS] COMMAND ...
Step Two: Install OpenLDAP
To ensure the completeness of best practices, this article provides the installation method of OpenLDAP. If you have already installed OpenLDAP, please skip this section.
Click to expand process description
Open the terminal command line window, create a file named
docker-compose.ymlin any directory, and open it with an editor (such as vim), copy and paste the following content and save exit, the explanation of each parameter is included in the comments of the file.version: '3'
services:
openldap:
image: osixia/openldap # Use the osixia/openldap image to start the OpenLDAP service.
container_name: openldap # The container name of OpenLDAP, which can be customized.
environment: # Configure environment variables.
- LDAP_ORGANISATION=Ninedata # The organization name of OpenLDAP, change NineData to your organization name.
- LDAP_DOMAIN=ninedata.com # The domain name of OpenLDAP, change to your own OpenLDAP service domain name.
- LDAP_ADMIN_PASSWORD=your_password # The administrator password of the OpenLDAP service.
ports: # Configure the service port of OpenLDAP.
- "389:389" # The LDAP service port based on plain text transmission, the default is 389.
- "636:636" # The LDAP service port based on SSL/TLS encrypted transmission, the default is 636.
volumes: # Map the /var/lib/ldap and /etc/ldap/slapd.d directories to the local ./data/ldap and ./data/slapd.d directories so that data can be saved persistently.
- ./data/ldap:/var/lib/ldap
- ./data/slapd.d:/etc/ldap/slapd.dGo to the directory where the
docker-compose.ymlfile is located, and execute the following command to pull and start the OpenLDAP service according to the parameters configured indocker-compose.yml:docker-compose up -dAfter execution, you can execute the
docker-compose pscommand to view the status of the OpenLDAP service, and if theSTATUScolumn displaysUp, it means it has started successfully.
Step Three: Install phpLDAPadmin
phpLDAPadmin is used to manage and operate user information in OpenLDAP, with an intuitive interface that can browse directory structure, search and edit entries in the directory, manage users, groups, and other LDAP objects.
Open the terminal command line window and execute the following command to pull the phpLDAPadmin Docker image:
docker pull osixia/phpldapadminCreate and start the phpLDAPadmin Docker container:
docker run --name phpldapadmin-container -p 6443:443 --env PHPLDAPADMIN_LDAP_HOSTS=192.168.2.33 --detach osixia/phpldapadminParameter Description--name phpldapadmin-container: Customize the name of the phpLDAPadmin container, wherephpldapadmin-containercan be replaced with your custom name.-p 6443:443: Map the local machine's port 6443 to the container's port 443 to access the phpLDAPadmin service through the local machine's port 6443, you can also replace 6443 with other port numbers.--env PHPLDAPADMIN_LDAP_HOSTS=192.168.2.33: Set the environment variablePHPLDAPADMIN_LDAP_HOSTS, which specifies the host address where the LDAP service is located, you need to replace192.168.2.33with your actual LDAP server address.--detach: Run the container in the background to prevent blocking the terminal.osixia/phpldapadmin: Specify the Docker image name to be run.
Access the phpLDAPadmin login page in the browser by visiting
https://<IP address>:<port>(in this example,https://192.168.2.33:6443), click on login in the left navigation bar, and then enter Login DN and Password on the right side, and click Authenticate to log in to the OpenLDAP system.IP address: Please fill in according to the actual
PHPLDAPADMIN_LDAP_HOSTSparameter value configured in the previous step.Port: Please fill in according to the actual
-pparameter value configured in the previous step.Login DN: Login information, usually composed of multiple RDNs (Relative Distinguished Name), each RDN consists of an attribute and attribute value pair, separated by commas. For example, a typical DN might be
cn=admin,dc=ninedata,dc=com. Wherecn=adminis the administrator user of the OpenLDAP system,dc=ninedataanddc=comare your own service domain names, these configuration information can be found in thedocker-compose.ymlfile in Step Two.Password: The administrator password of the OpenLDAP service, which can also be found in the
docker-compose.ymlfile in Step Two.
tip- Due to self-signed certificate issues, the browser may block your access when visiting for the first time, at this point, you need to click on Advanced, and then click on Continue to 192.168.2.33 (unsafe). This example is based on the Chrome browser, the prompt information of different browsers is different, please refer to the actual situation.
- If the browser prompts that the page cannot be opened, or reports an
ERR_INVALID_HTTP_RESPONSEerror, please make sure that the URL prefix you are using ishttps://, nothttp://.
Since this example is a newly installed OpenLDAP, there is no data, we add an organization to OpenLDAP through phpLDAPadmin and add a user data record in the organization.
- Create Organizational Unit (ou)
- Create User in Organization (cn)
Click on the domain name in the left navigation bar, and click on Create a child entry on the right page.
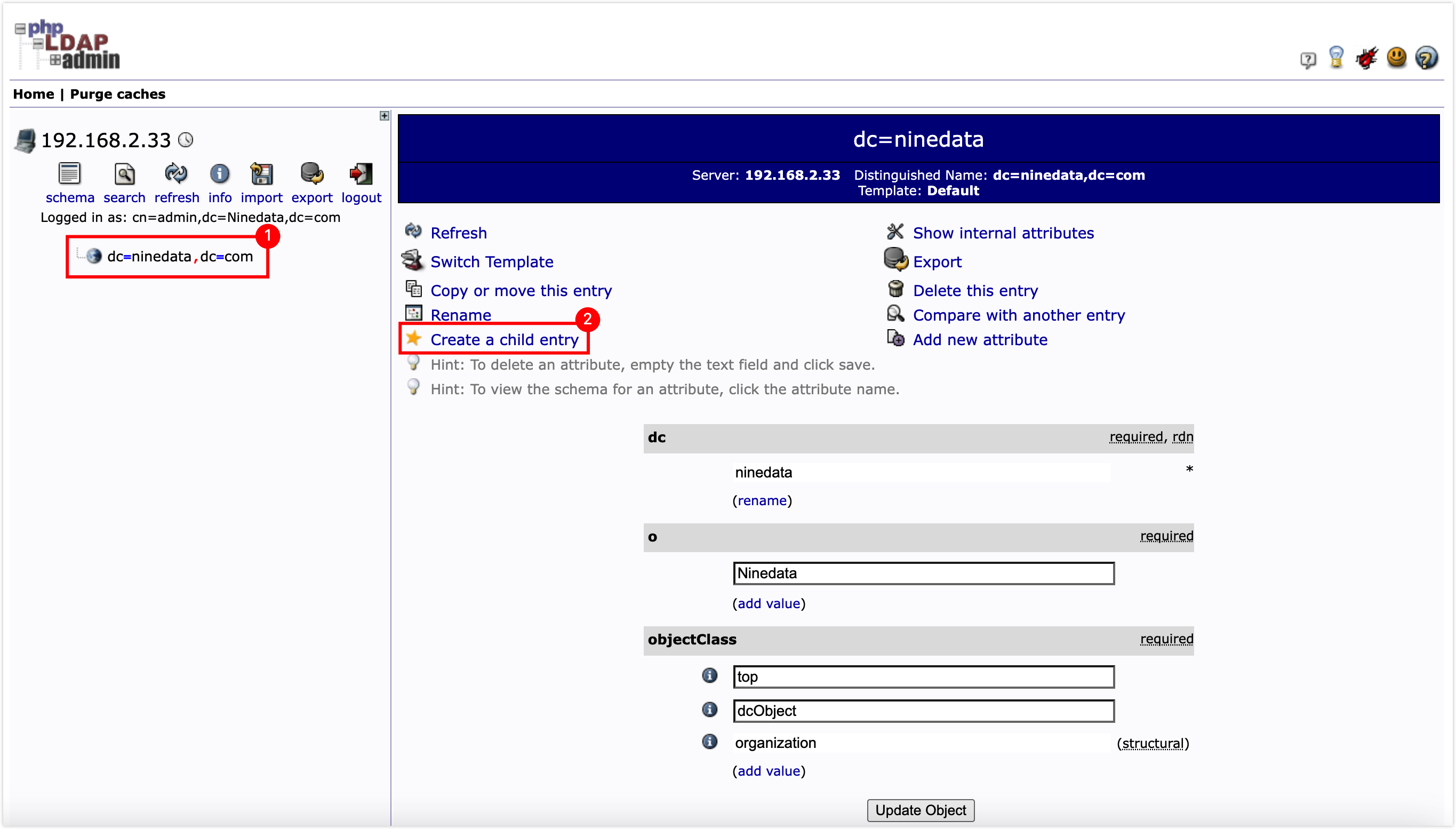
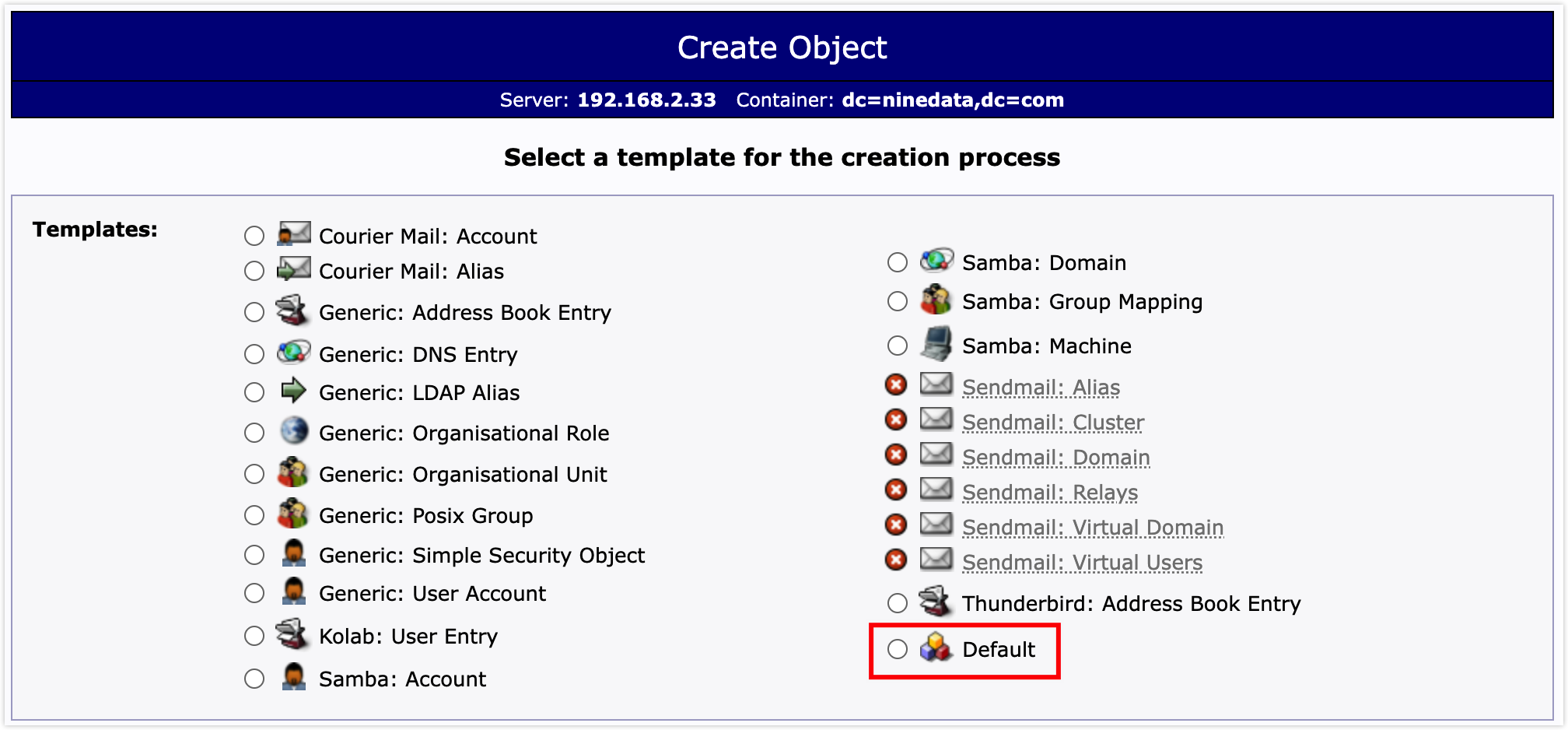
On the page to select the creation template, click on Default.
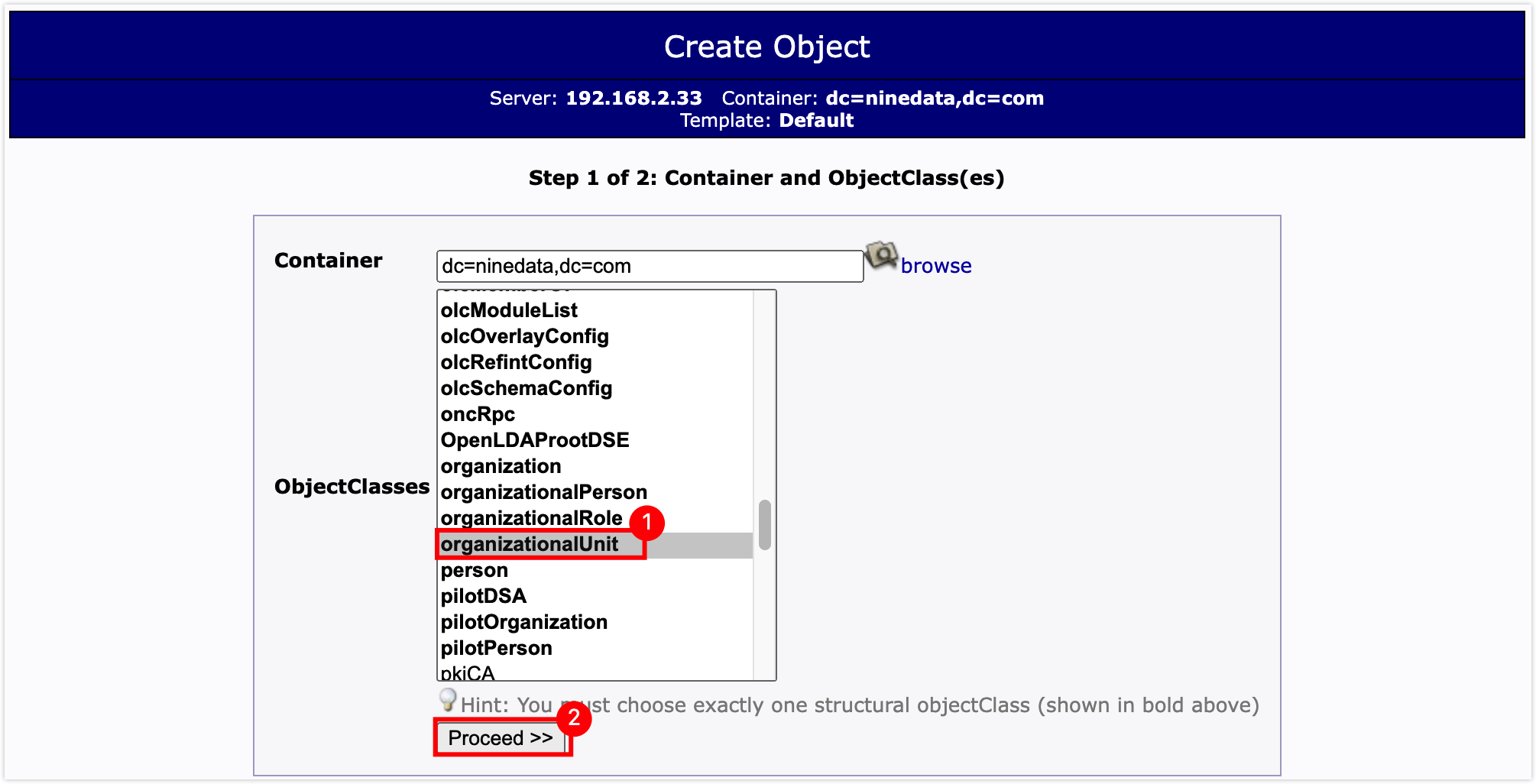
In the ObjectClasses list, select organizationalUnit, and then click the Proceed >> button.
In the attribute configuration window, set RDN to ou (ou), and enter the name of the organizational unit in the text box below ou, then scroll to the bottom of the page and click the Create Object button.
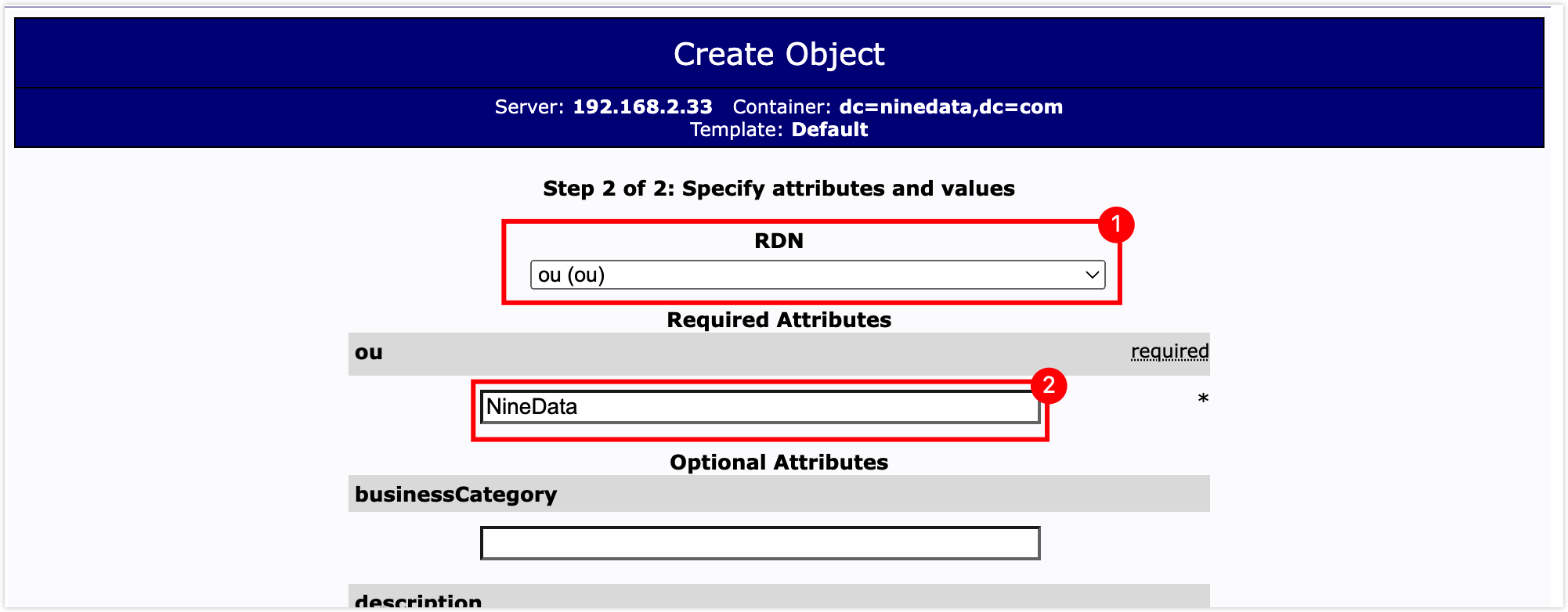 tip
tipYou can supplement other information of the organizational unit as needed.
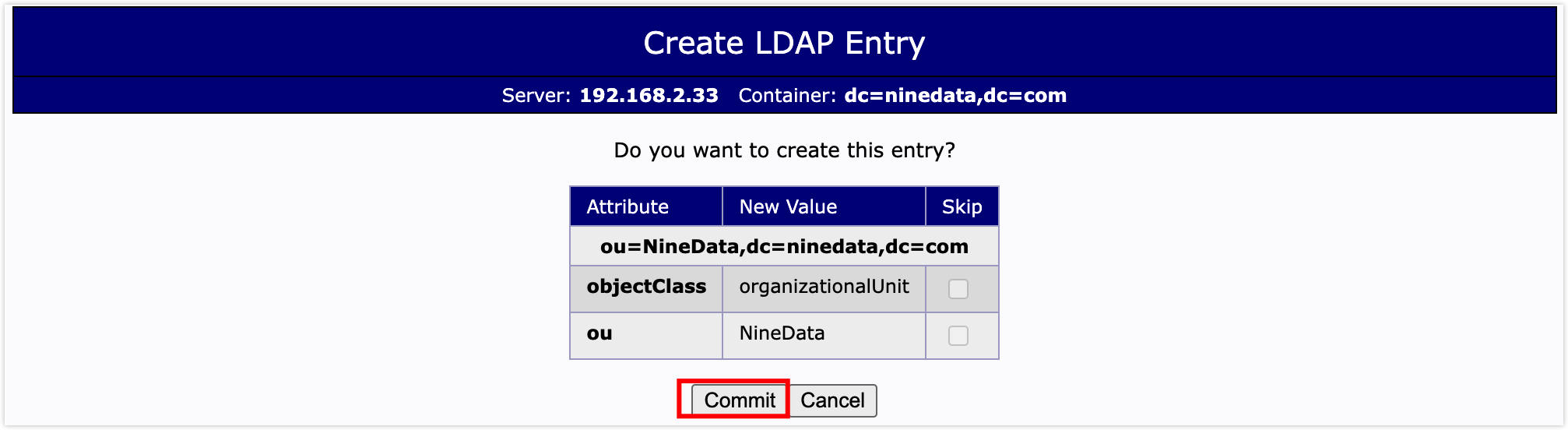
On the confirmation page, click Commit.
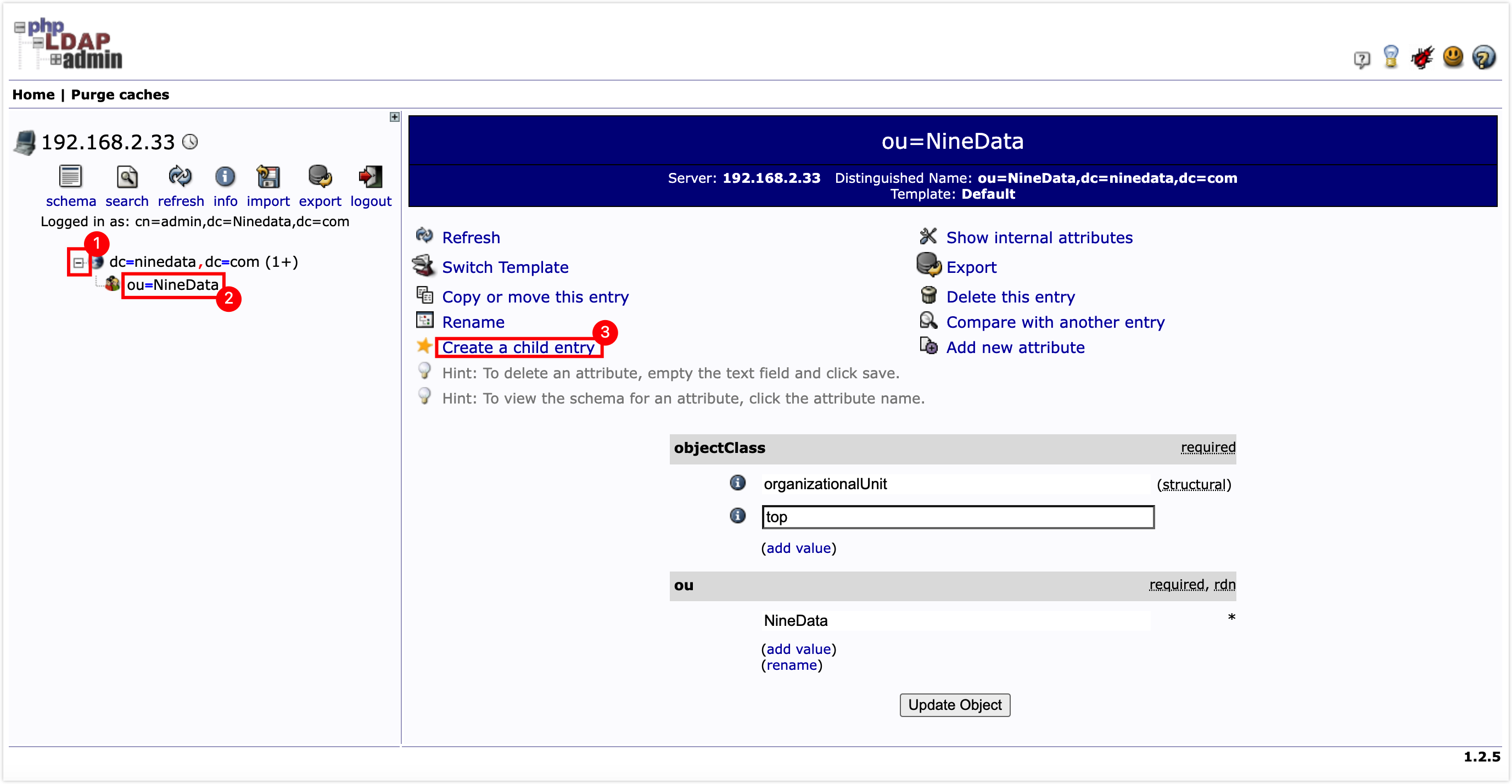
Click on the organizational unit under the domain name in the left navigation bar, and click on Create a child entry on the right page.
On the page to select the creation template, click on Default.
In the ObjectClasses list, select inetOrgPerson, and then click the Proceed >> button.
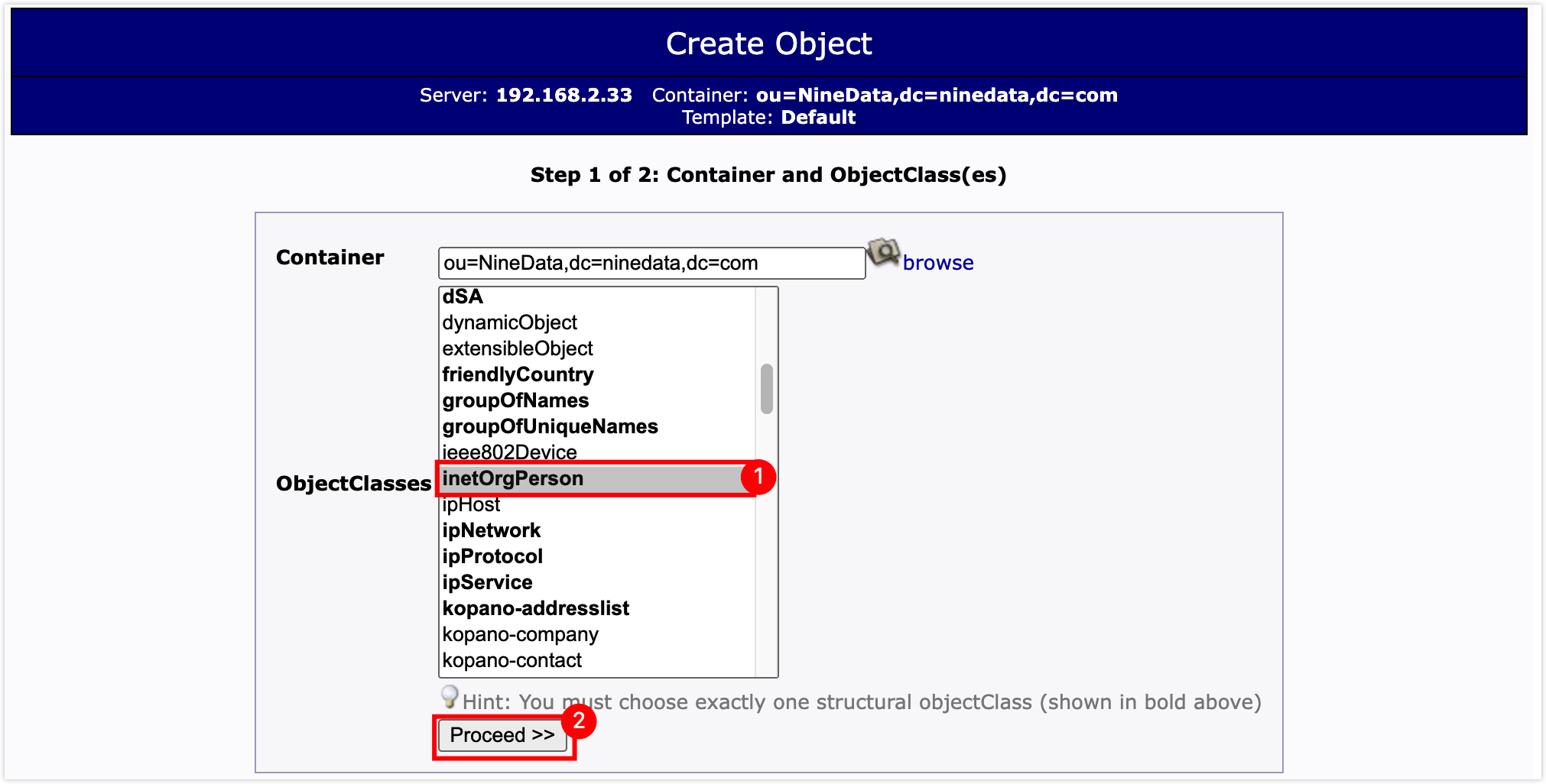
In the attribute configuration window, set RDN to cn (cn); enter the user's common name in the text box below cn; enter the user's surname in the text box below sn, and enter the user password in the text box below Password, then scroll to the bottom of the page and click the Create Object button.
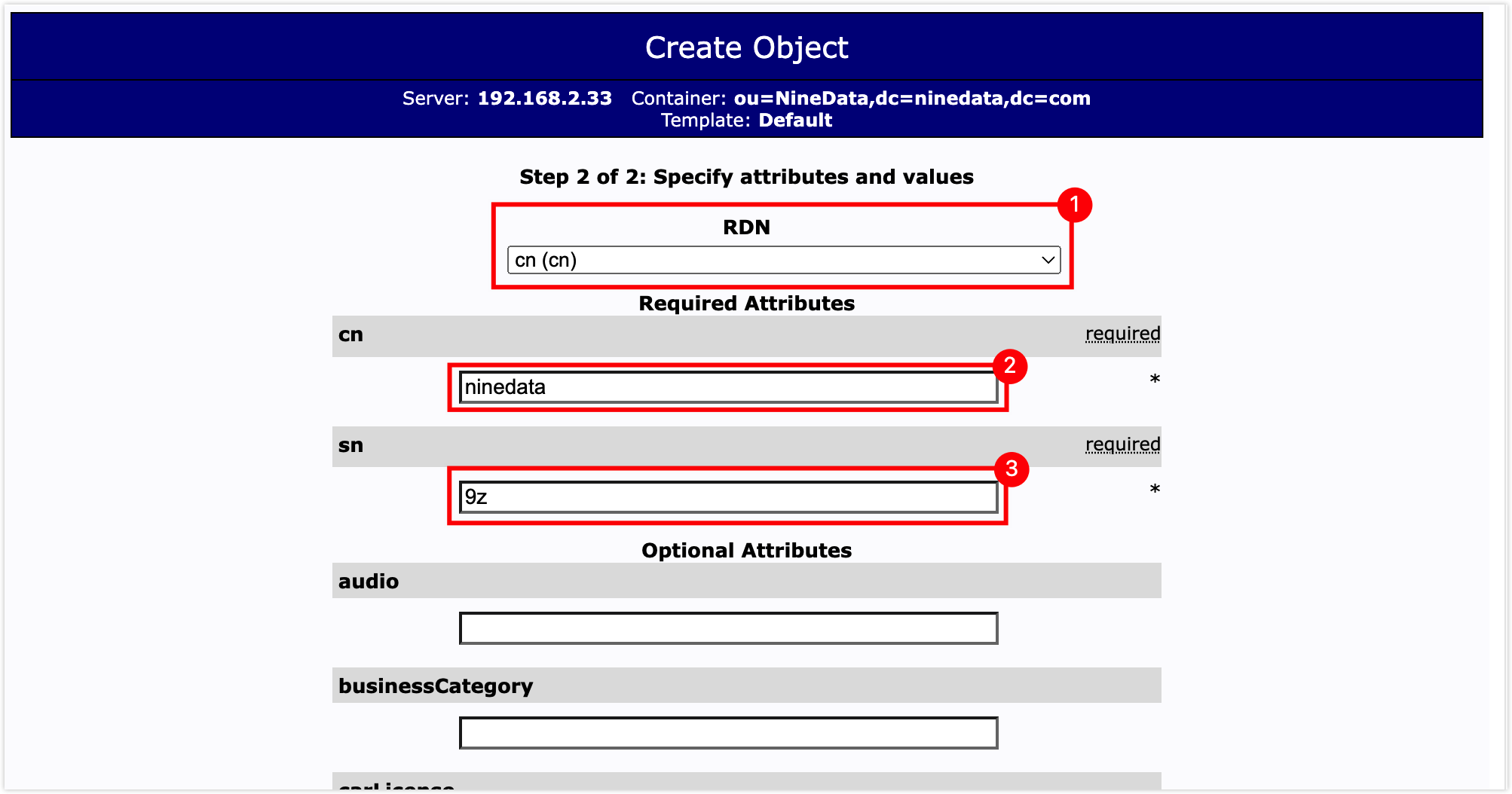
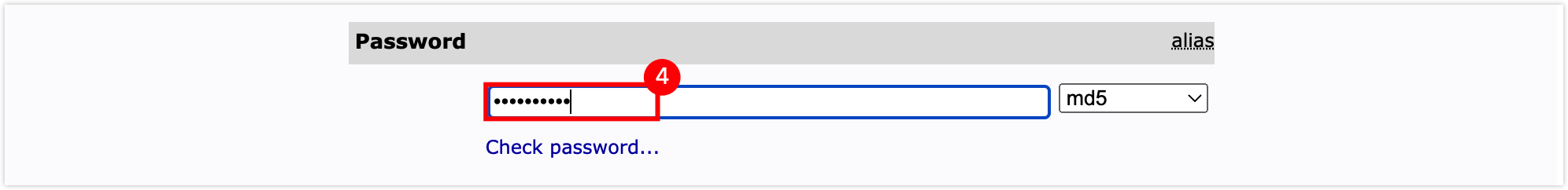 tip
tipYou can supplement other user information as needed.
On the confirmation page, click Commit to complete the user creation.
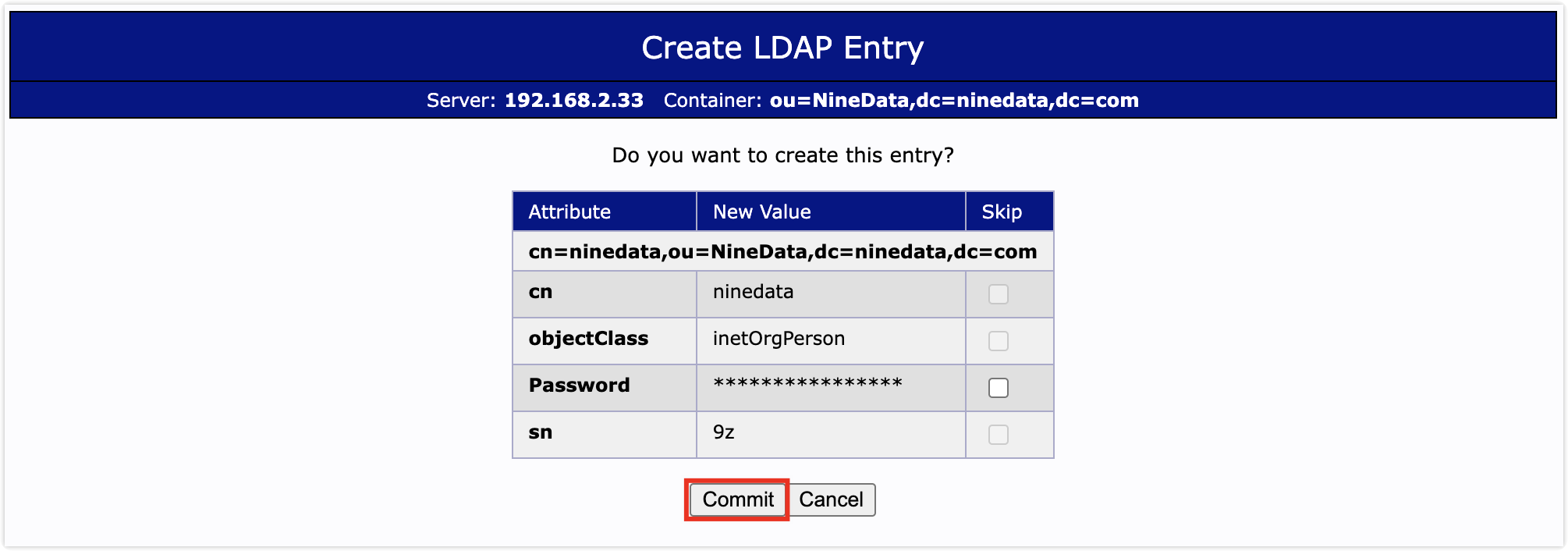
Add the User Name attribute as the unique identifier for the user to log in to the system. In the left navigation bar, select the newly created user, and click Add new attribute on the right page.
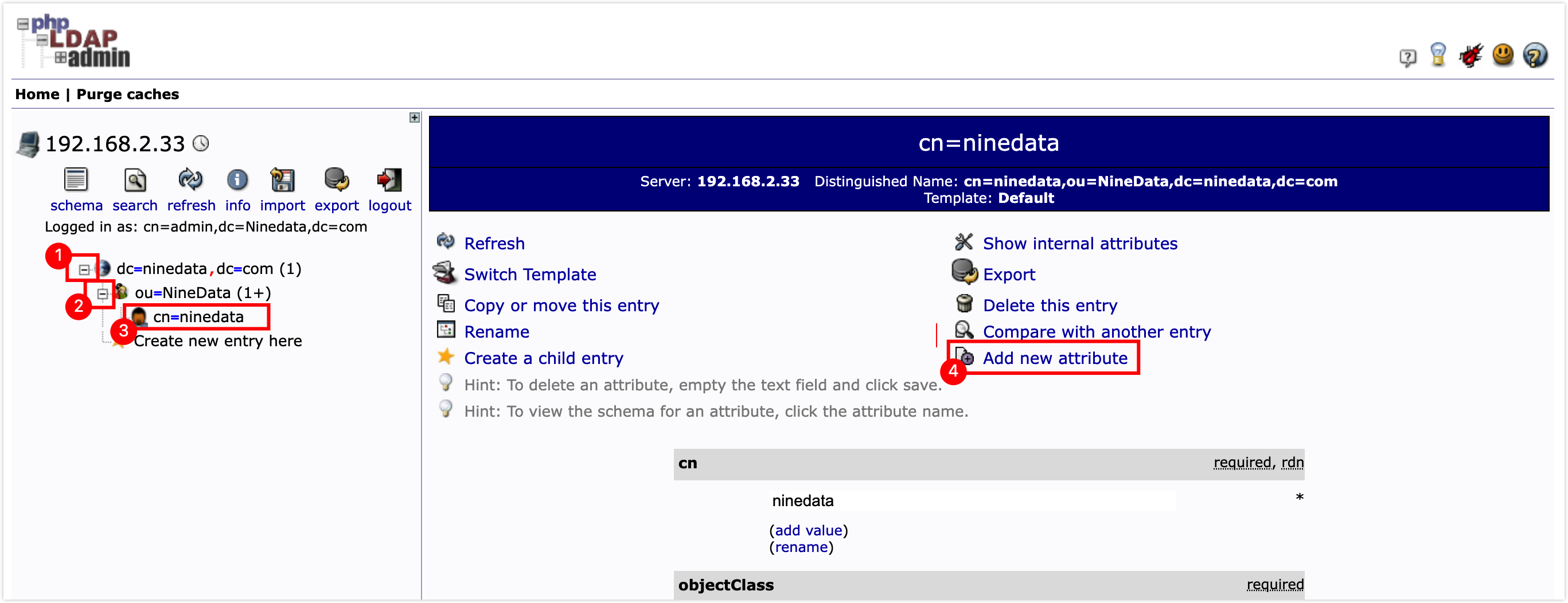
In the attribute configuration window, set RDN to User Name, enter the user's unique identifier in the text box below the added User Name attribute, you can customize this identifier, then scroll to the bottom of the page and click Update Object.
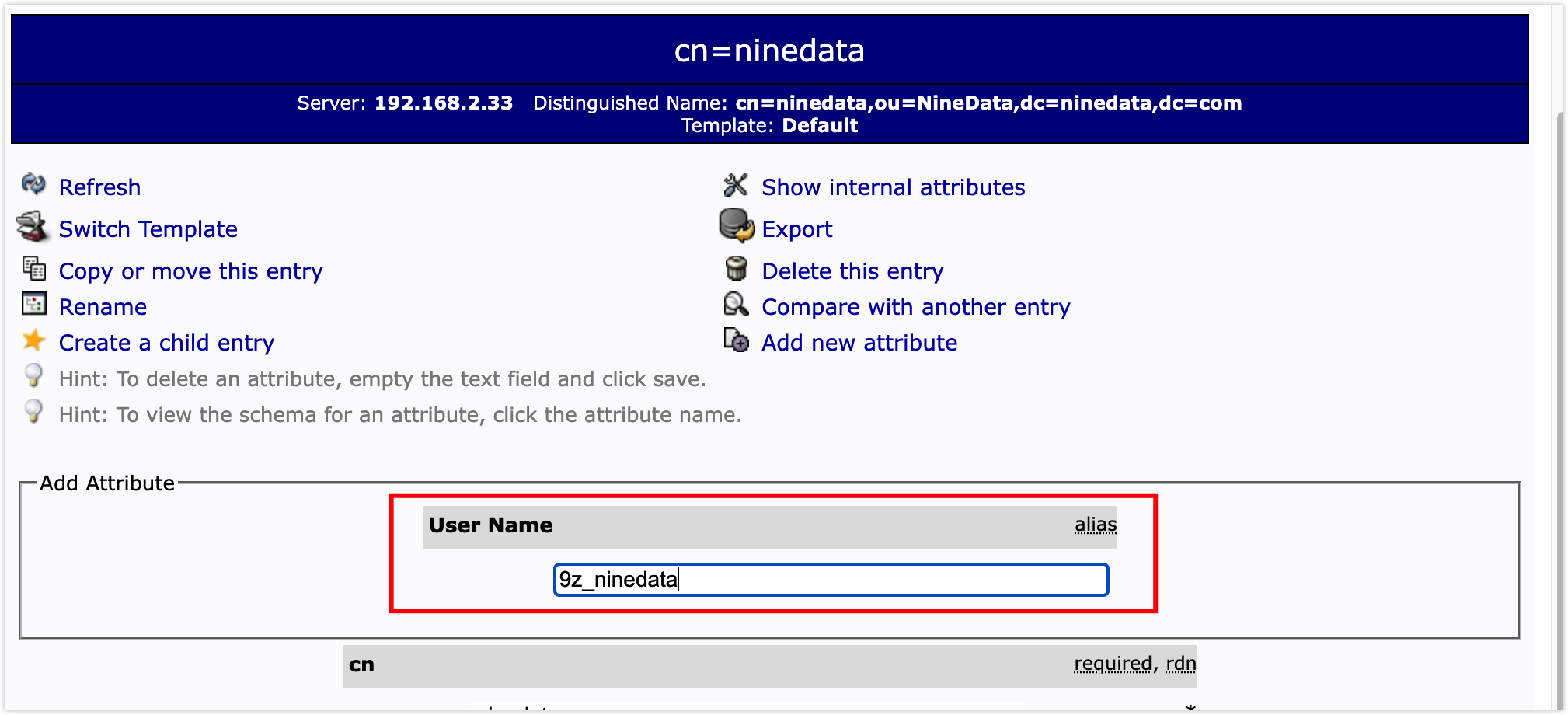
On the confirmation page, click Update Object to complete the addition of user attributes.
Step Four: Install KeyCloak and Synchronize User Data from OpenLDAP
Keycloak is an open-source identity and access management solution that provides authentication, authorization, and single sign-on (SSO) features. This section introduces how to use KeyCloak to synchronize user data from OpenLDAP for SSO access.
Open the terminal command line tool and execute the following command to pull KeyCloak.
docker pull jboss/keycloak:9.0.0Create and start the KeyCloak container.
docker run --name keycloak-container -p 8443:8443 --env KEYCLOAK_USER=admin --env KEYCLOAK_PASSWORD=admin --detach jboss/keycloak:9.0.0Parameter Description--name keycloak-container: Customize the name of the KeyCloak container, wherekeycloak-containercan be replaced with your custom name.-p 8443:8443: Map the local machine's port 8443 to the container's port 8443 to access the KeyCloak service through the local machine's port 8443, you can also replace the local machine's 8443 port with other port numbers.--env KEYCLOAK_USER=admin: Set the environment variableKEYCLOAK_USER, which specifies the KeyCloak service administrator account asadmin, you can customize this account.--env KEYCLOAK_PASSWORD=admin: Set the environment variableKEYCLOAK_PASSWORD, which specifies the KeyCloak service administrator password asadmin, you can customize this password.--detach: Run the container in the background to prevent blocking the terminal.jboss/keycloak:9.0.0: Specify the Docker image name to be run.
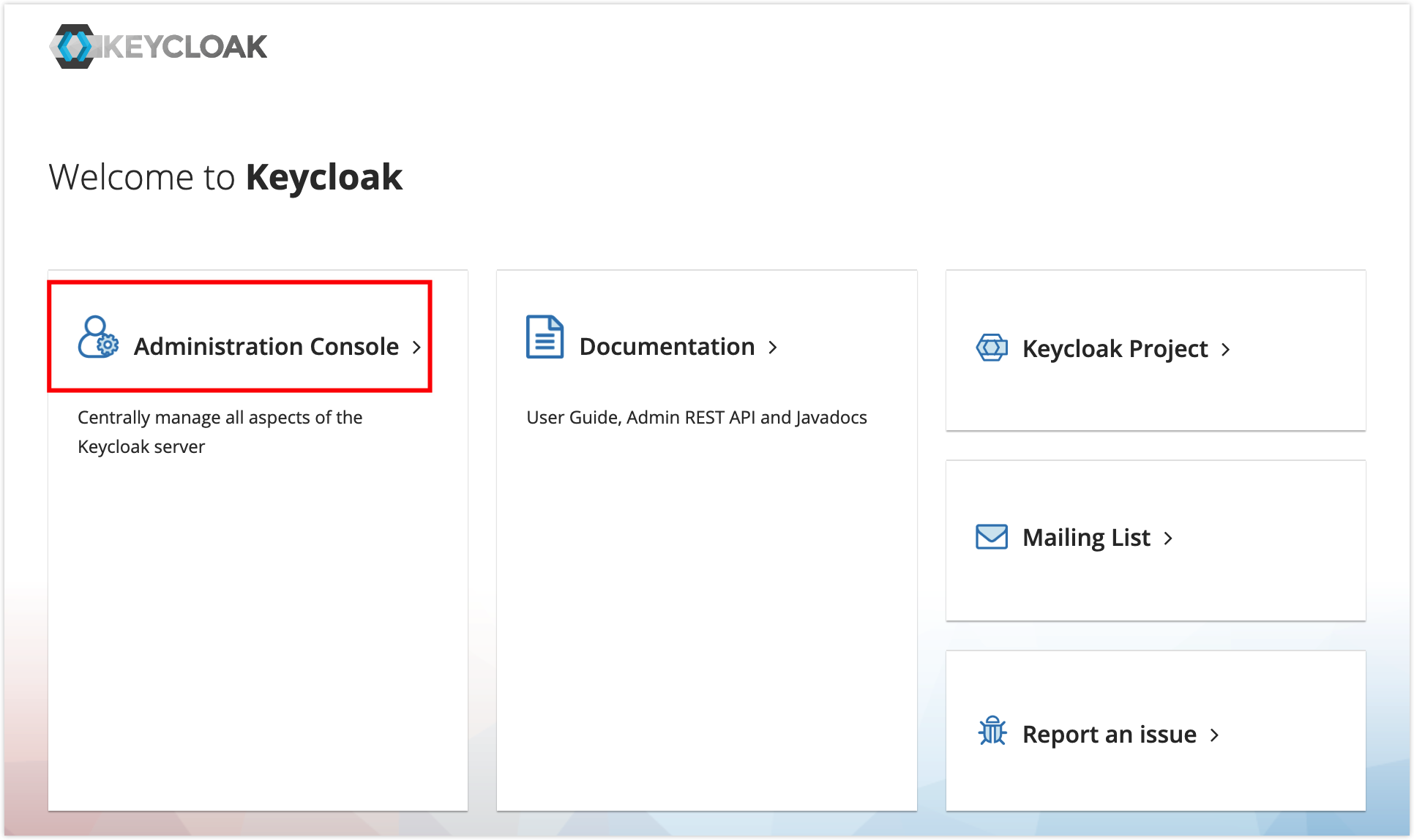
Access the KeyCloak welcome page by visiting
https://<IP address>:<port>in the browser (in this example,https://192.168.2.33:8443), and click on Administration Console to enter the login page.- IP address: Please fill in according to the actual host address where the KeyCloak service is installed.
- Port: Please enter according to the value of the
-pparameter you actually configured in the previous step.
 tip
tip- Due to self-signed certificate issues, the browser may block your access when visiting for the first time, at this point, you need to click on Advanced, and then click on Continue to 192.168.2.33 (unsafe). This example is based on the Chrome browser, the prompt information of different browsers is different, please refer to the actual situation.
- If the browser prompts that the page cannot be opened, or reports an
ERR_INVALID_HTTP_RESPONSEerror, please make sure that the URL prefix you are using ishttps://, nothttp://.
On the login page, enter the login account and password, and click Log In.
- Login account: Please enter according to the
KEYCLOAK_USERparameter value you passed in the previous step, the login account in this example isadmin. - Password: Please enter according to the
KEYCLOAK_PASSWORDparameter value you passed in the previous step, the password in this example isadmin.
- Login account: Please enter according to the
(Optional) Enable the Chinese interface.
Click on Realm Settings in the left navigation bar, and click on the Themes tab on the right page, configure in the following order and log out of the system to apply the configuration.
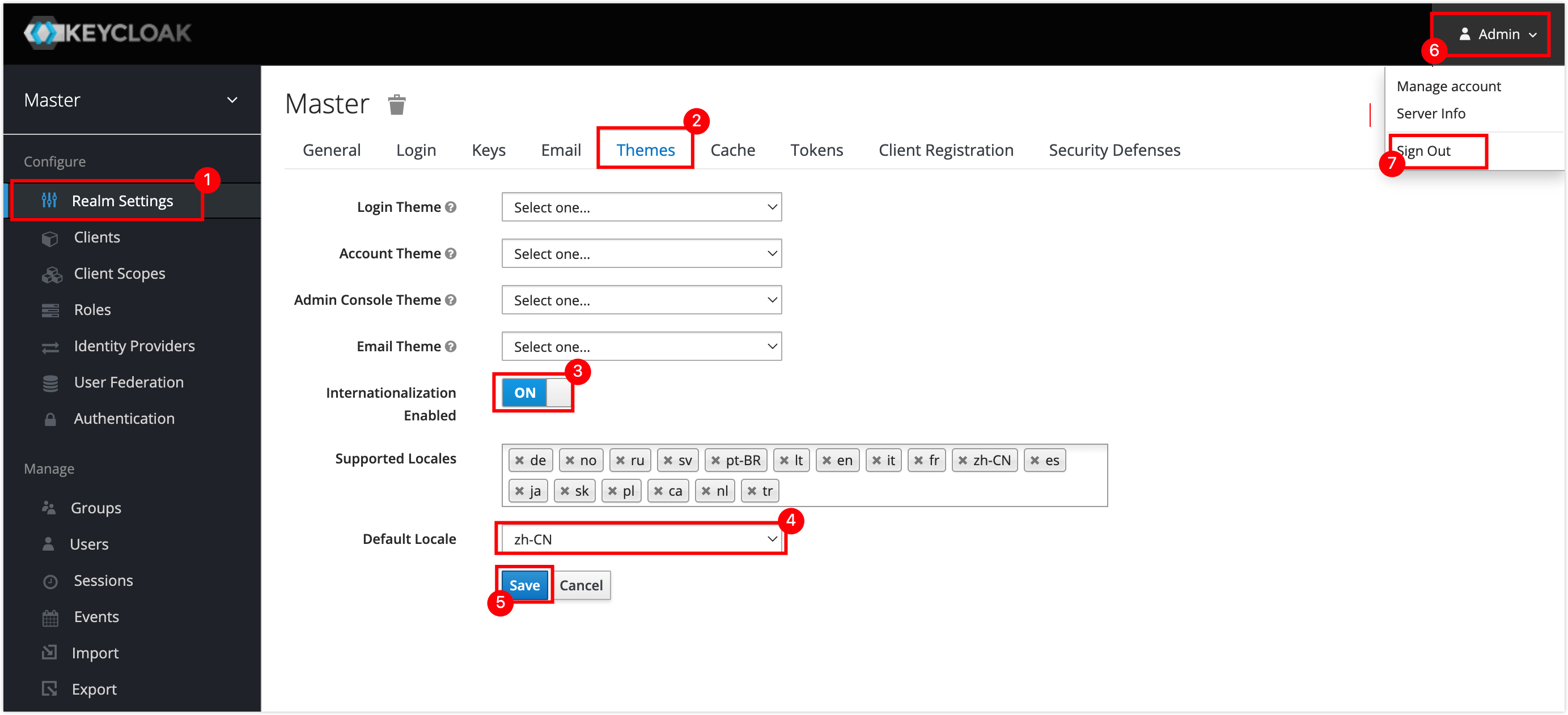
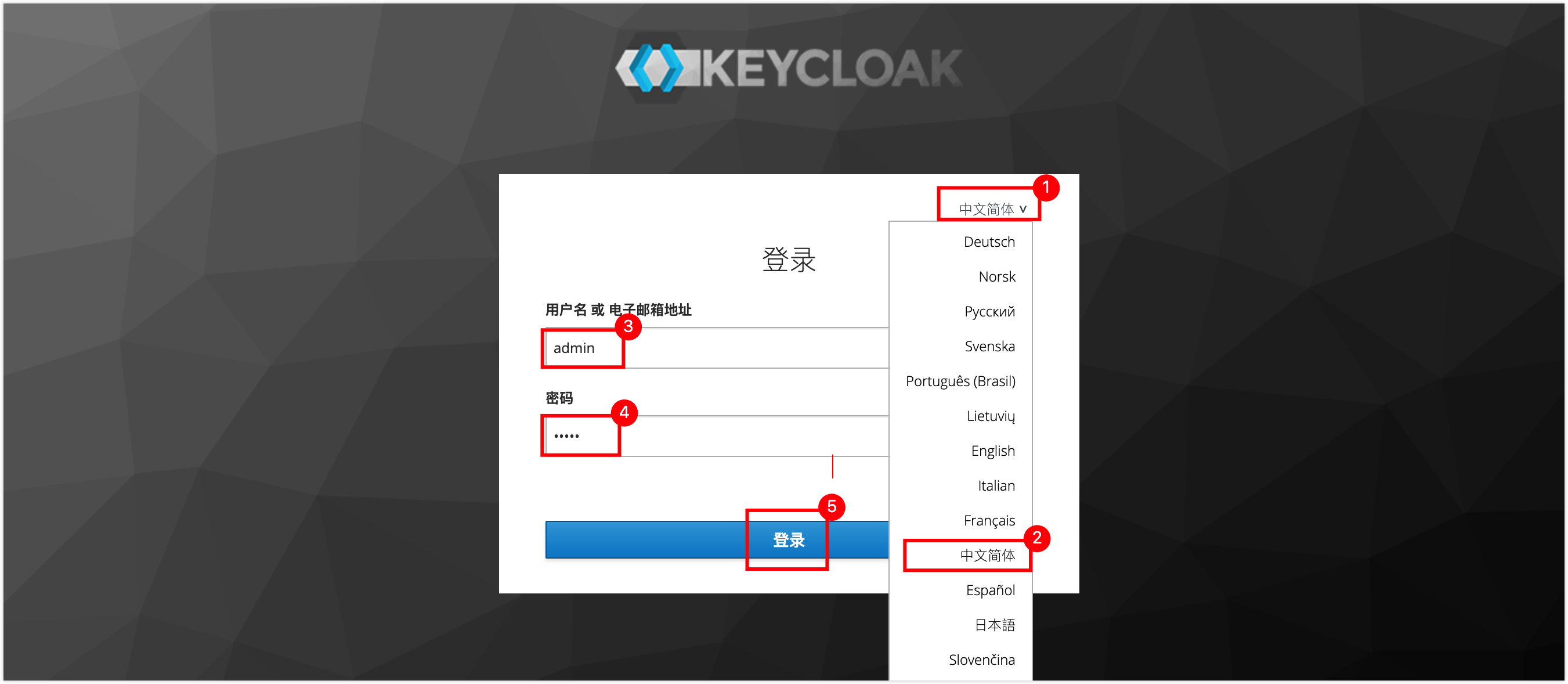
Switch the language once, and then log back into KeyCloak.
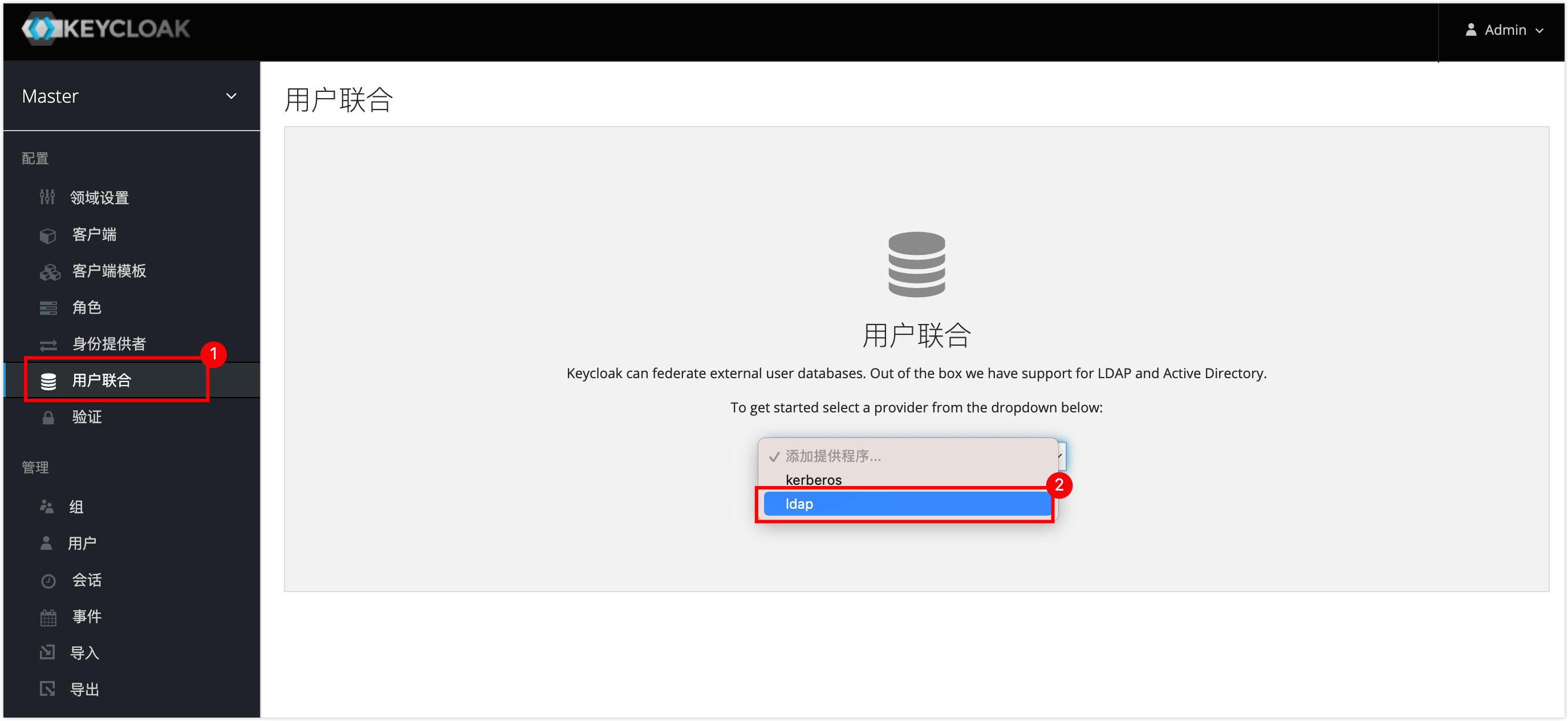
In the left navigation bar, click on User Federation, and select ldap as the user database.
On the Add User Federation Provider page, configure according to the following order.
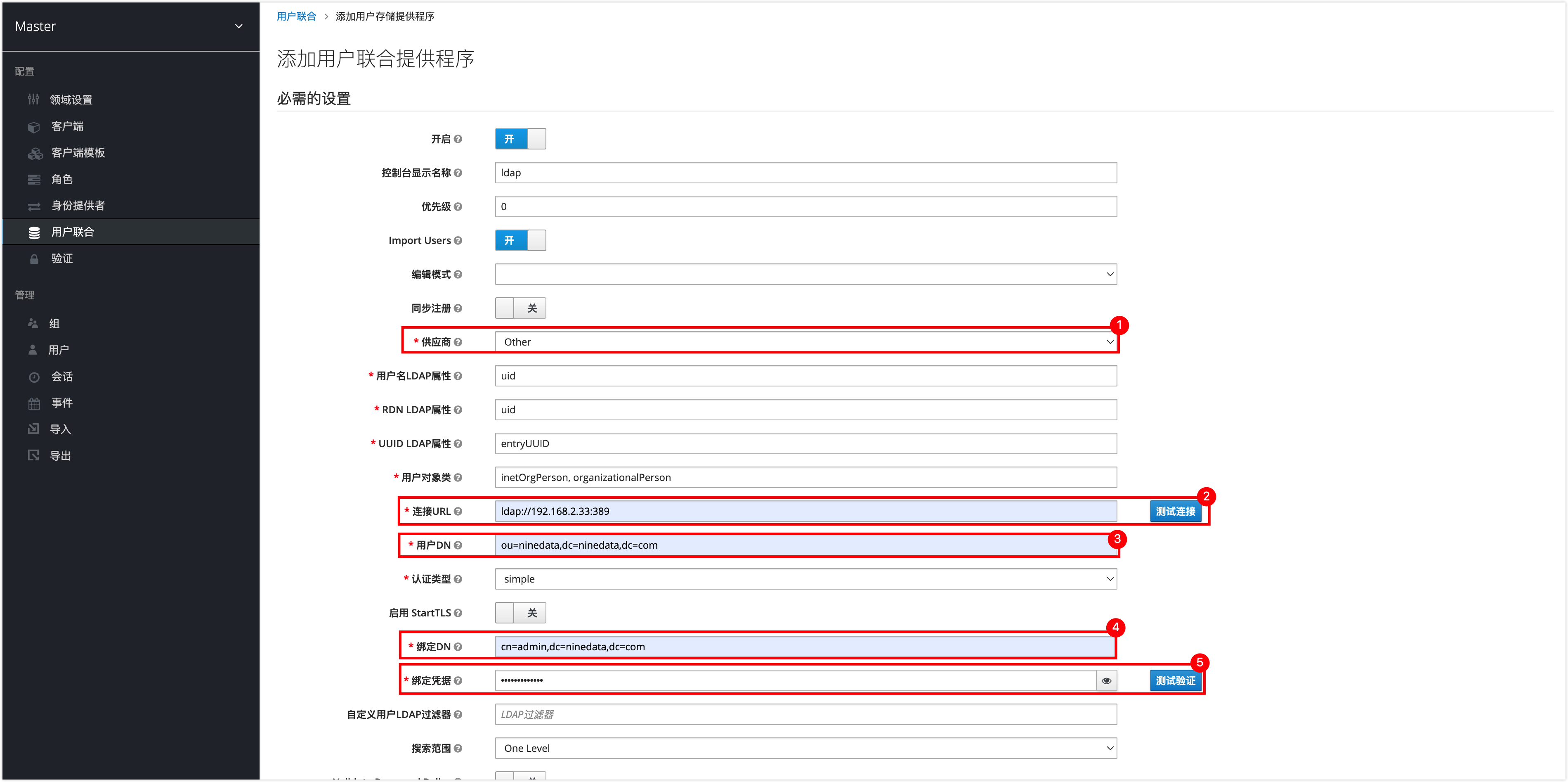
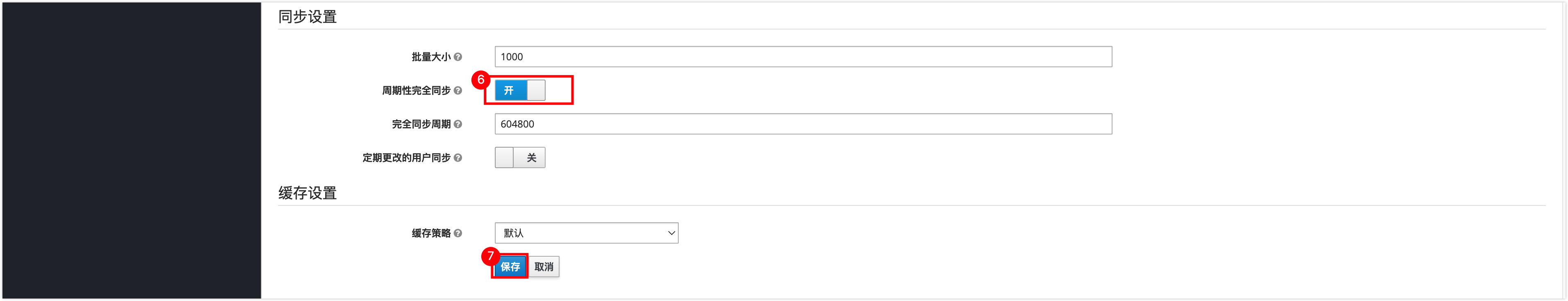
Number Description 1 Select ldap as the provider. 2 Enter the connection address of the OpenLDAP service, format: ldap://<OpenLDAP server IP>:<port>. After entering, you can click Test Connection to test the connectivity.3 Composed of the organization name and domain name, format: ou=<Organization Name>,dc=<Service Domain Name>,dc=<Service Domain Name>. Example:ou=ninedata,dc=ninedata,dc=com.4 Composed of the administrator username and domain name, format: cn=<Administrator Username>,dc=<Service Domain Name>,dc=<Service Domain Name>. Example:cn=admin,dc=ninedata,dc=com.5 Enter the administrator password for accessing OpenLDAP. 6 Enable Periodic Full Sync to periodically synchronize the added, deleted, and modified member information in OpenLDAP automatically. 7 Save changes. After clicking Save, the page will prompt Success! The provider has been created. which means it has been added successfully, click Sync All Users to synchronize the user information in your OpenLDAP to KeyCloak.
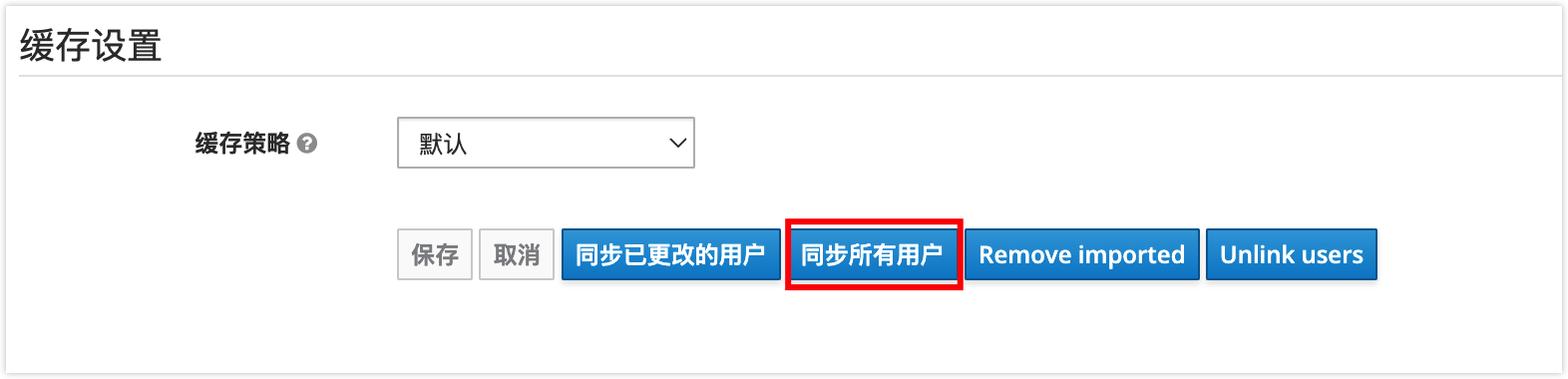
In the left navigation bar, click on Realm Settings, right-click on SAML Metadata and save it as a
.xmlfile for later use.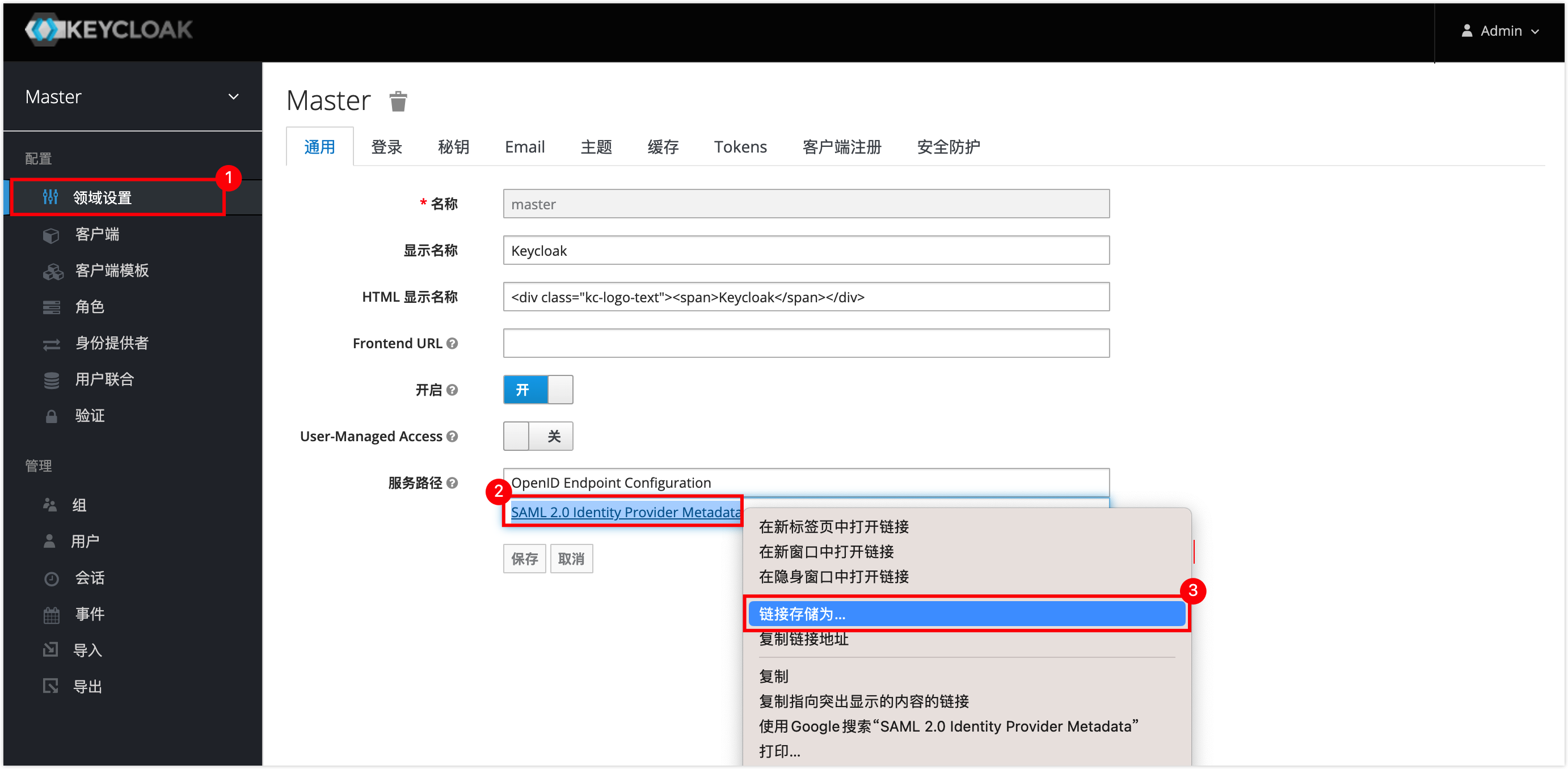
Step Five: Configure NineData SSO Login
Prerequisites
Your role is "Administrator". For more information about roles, please refer to Roles.
Operation Steps
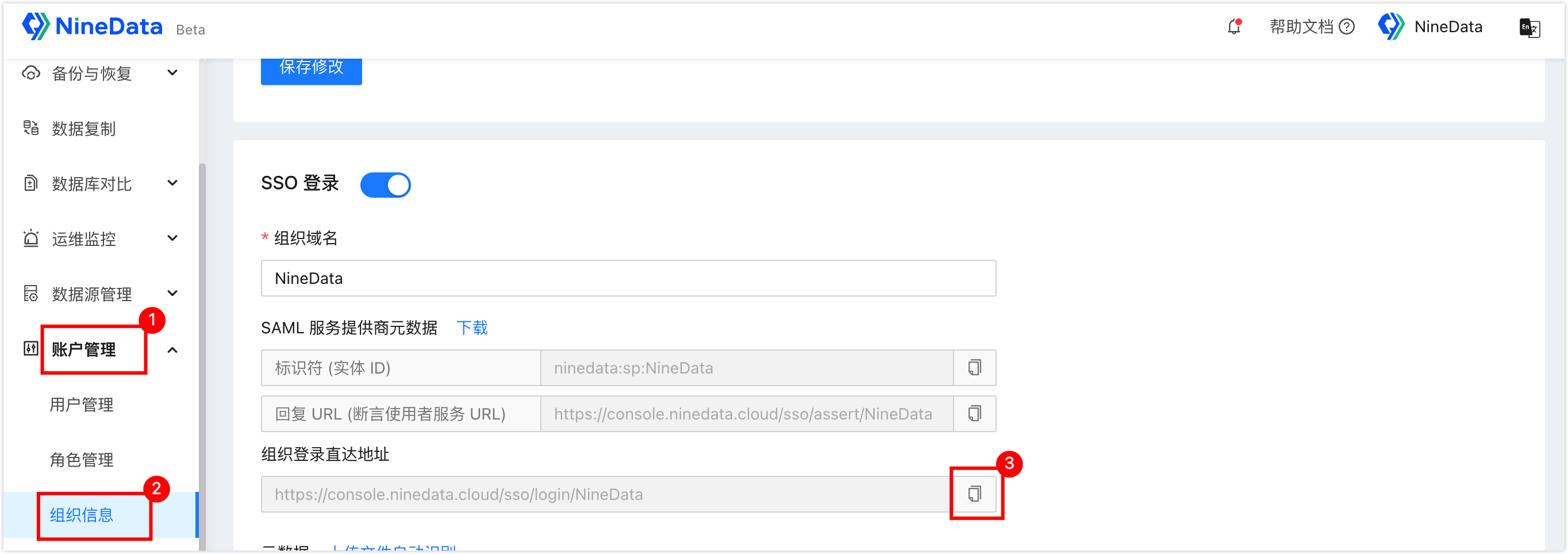
- Click on Account > **Organization** in the left navigation bar, and configure SSO according to the following order.
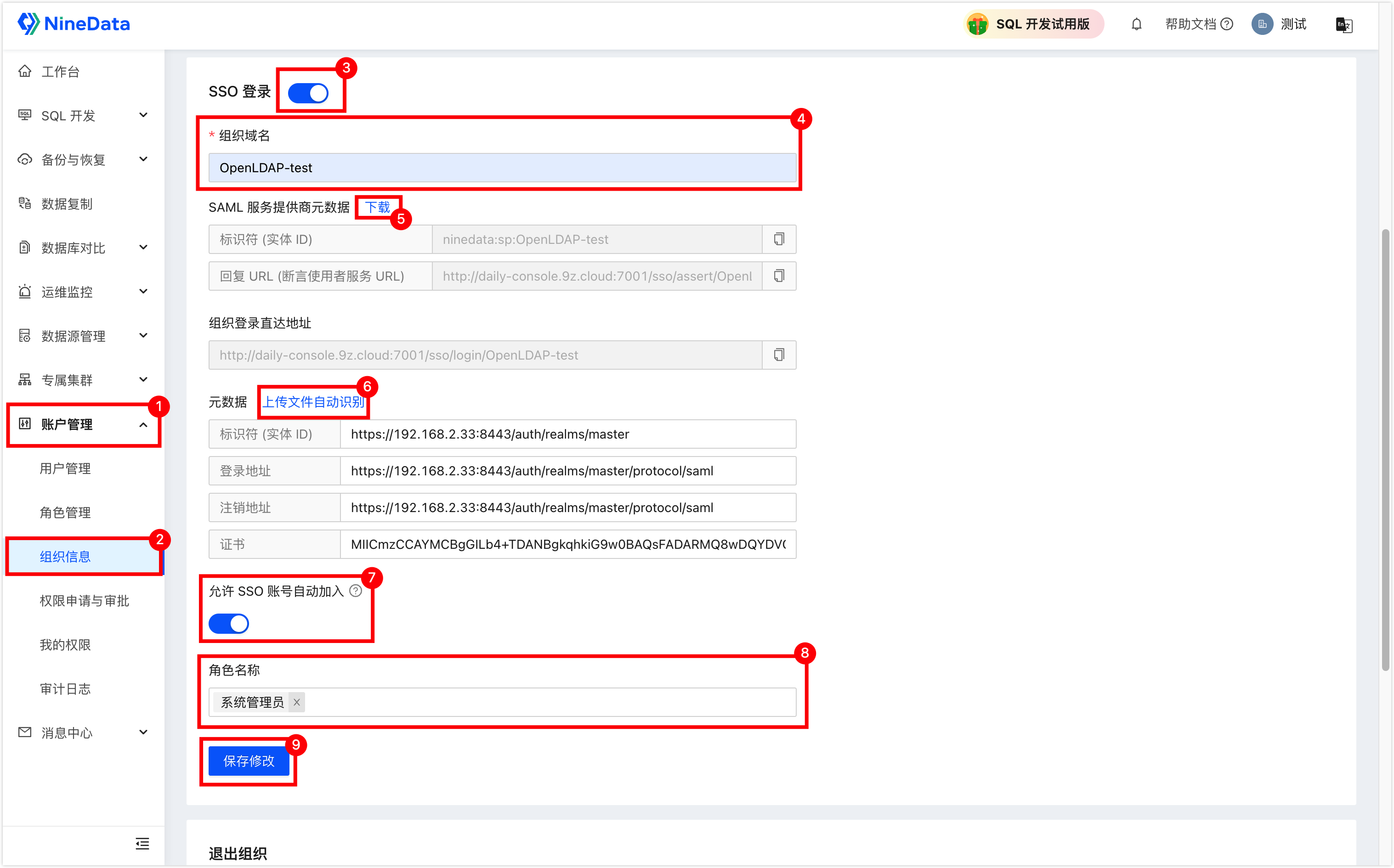
Number Description 3 Turn on the SSO login switch. 4 Enter the SSO organization name, after entering, SAML Service Provider Metadata will automatically generate Identifier (Entity ID) and Reply URL (Assertion Consumer Service URL) below. 5 Download the metadata file for later use. 6 Click Upload File to Auto-recognition, select the SAML metadata downloaded from KeyCloak, and automatically recognize and fill in the information below. 7 Turn on this option, and when users log in to NineData through the SSO method, the system will automatically add the user to NineData, you don't need to create SSO users in advance in the NineData console. 8 Optional when Allow SSO Account Auto-join is turned on, specify the default role bound to the automatically joined SSO user, support for single and multiple selections. 9 Save changes. Log in to KeyCloak with the administrator account (the account password in this example: admin/admin), click on Clients in the left navigation bar, and click Create in the upper right corner of the page.
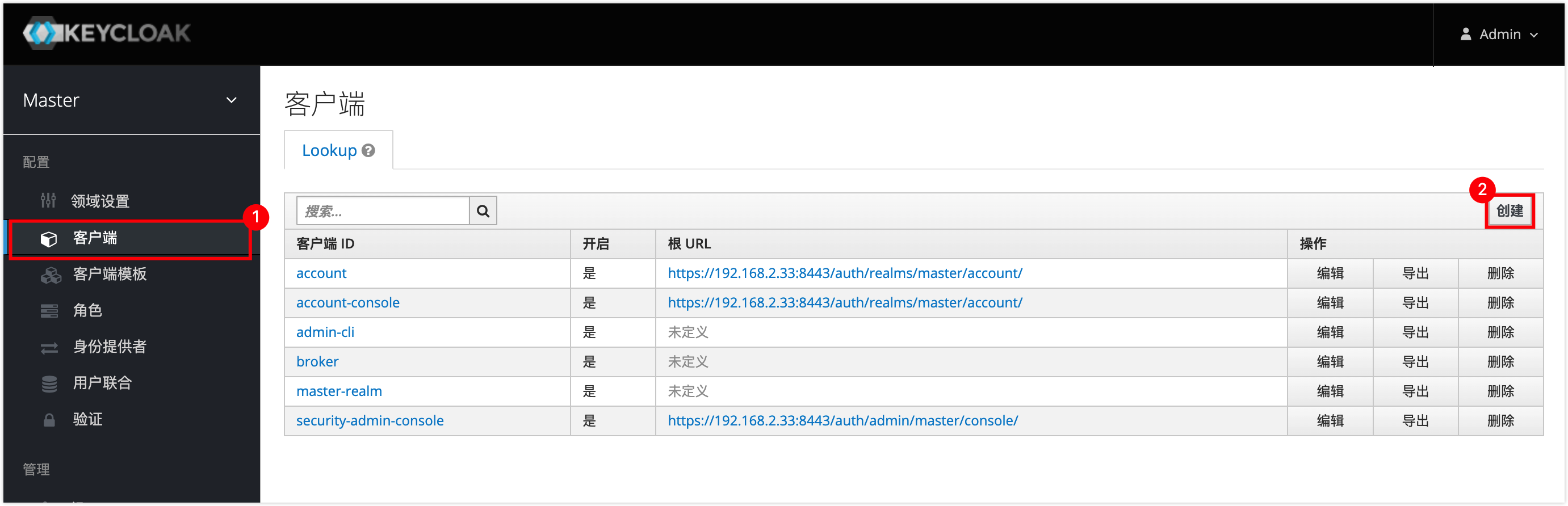
On the Add Client page, click Select File, import the
.xmlmetadata file downloaded from the NineData console (Step 1, Number 5), click Save to automatically jump to the current client's configuration page, find and turn off the Require Client Signature switch, scroll to the bottom of the page, and click Save.Click on Account > Organization in the left navigation bar, and copy the Org Login URL on the page to provide to the corresponding user. The user can log in to NineData by logging in to KeyCloak with their own account.
Step Six: Users Log in to NineData via SSO
Prerequisites
Users have obtained Org Login URL from the administrator.
Operation Steps
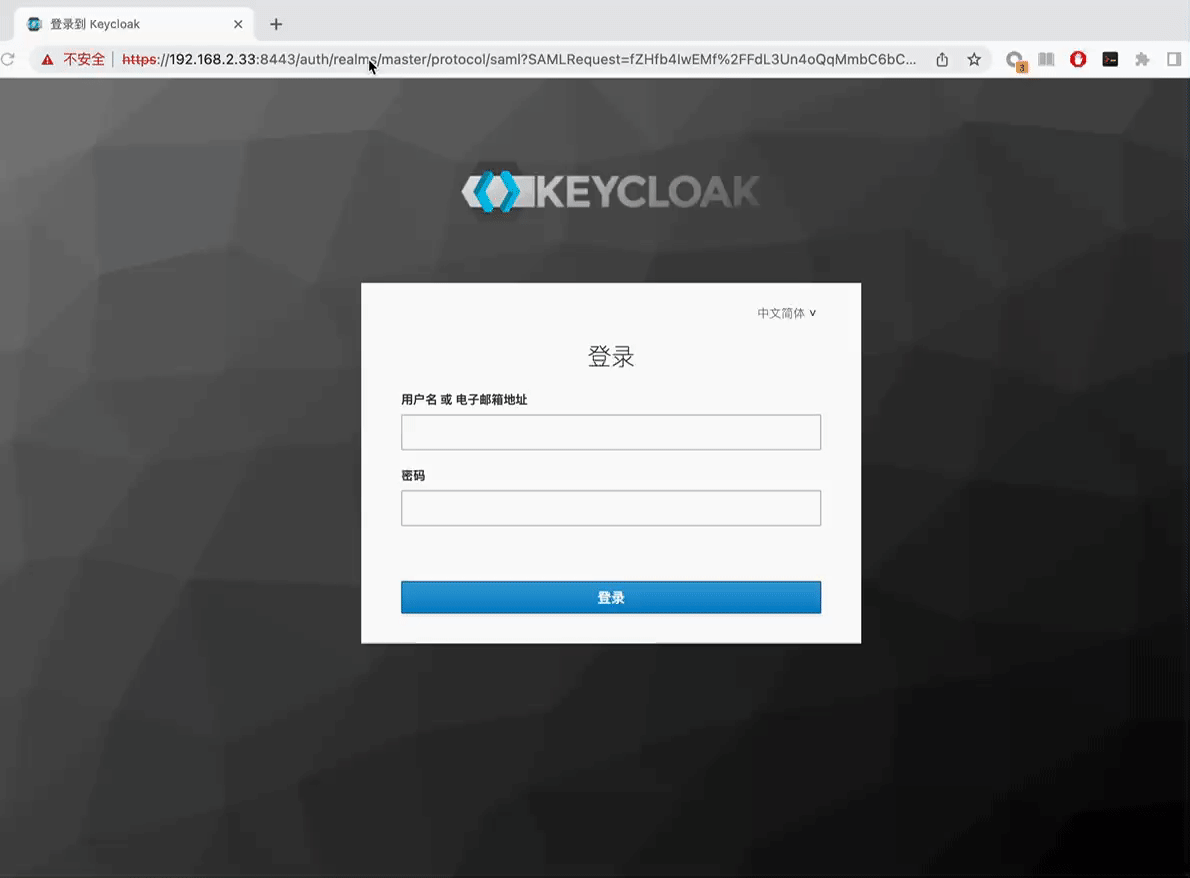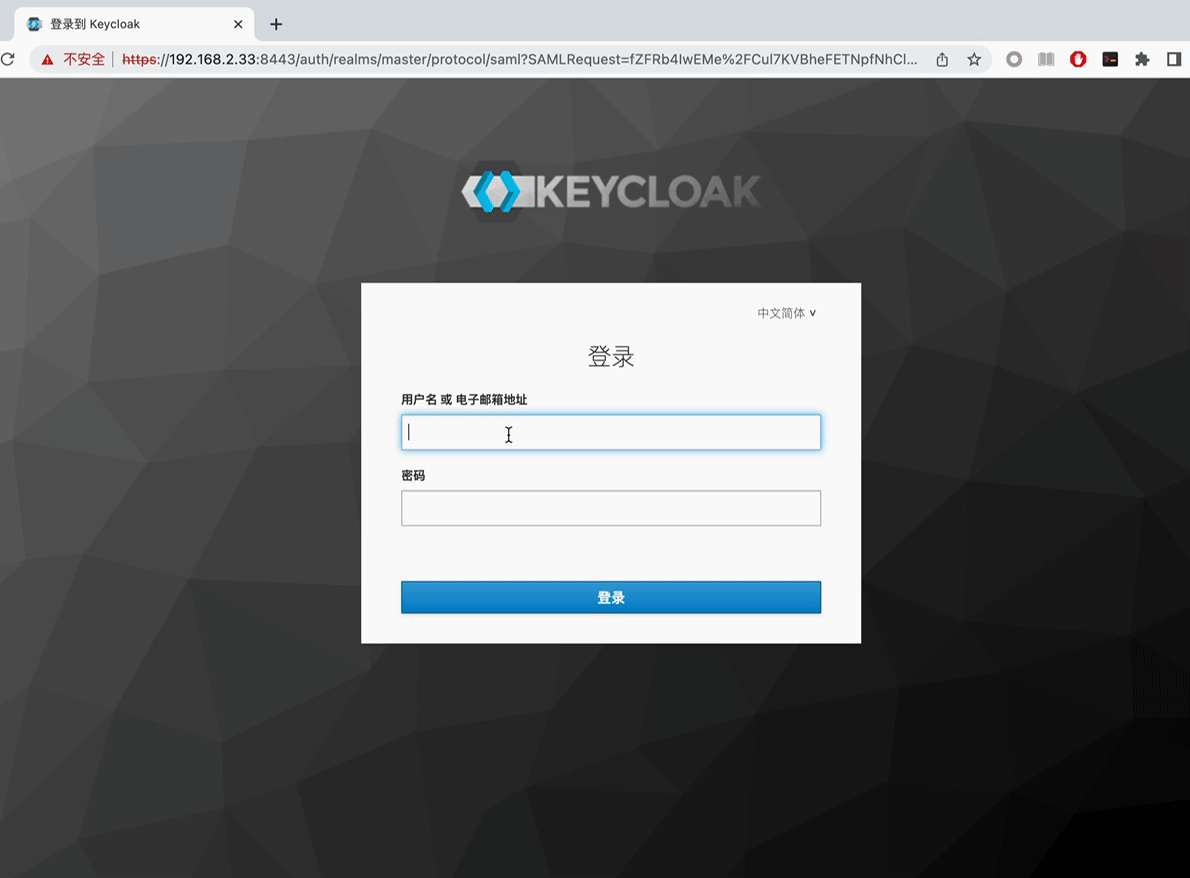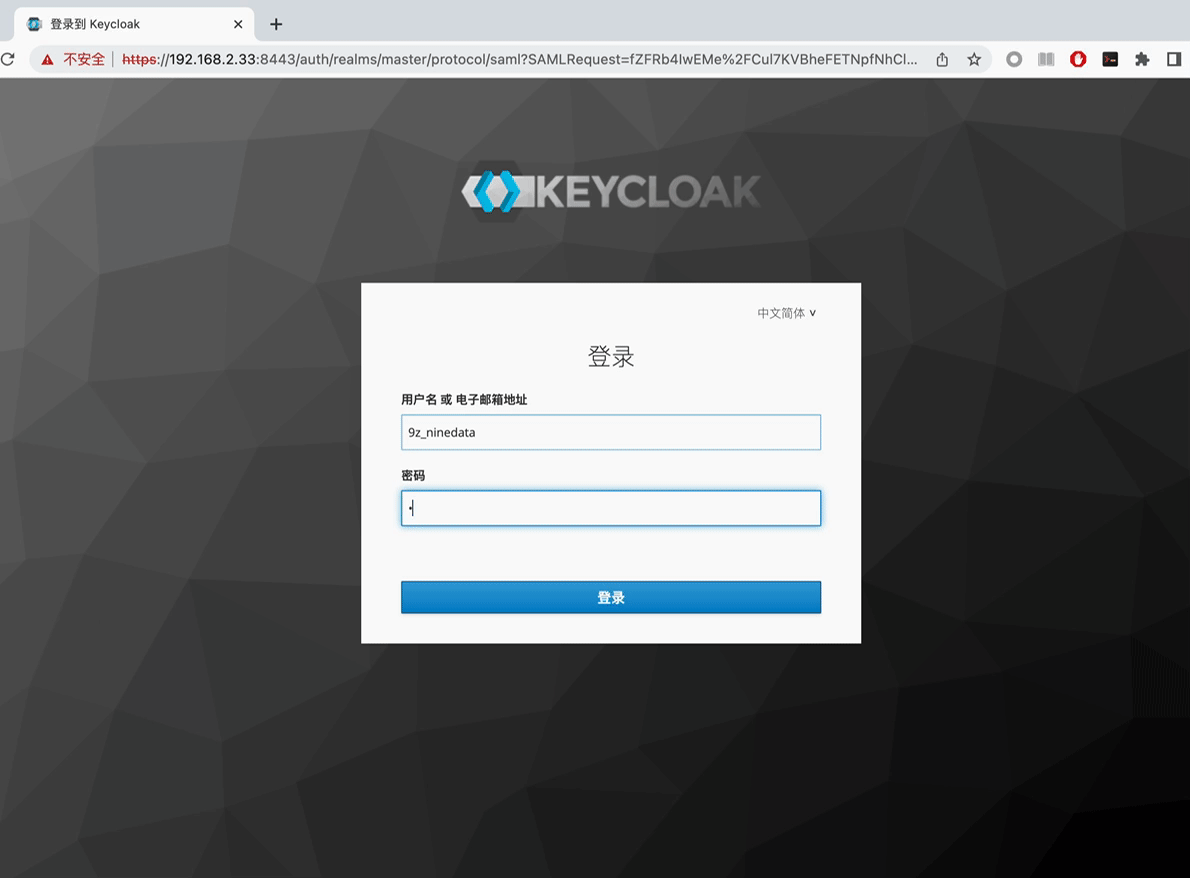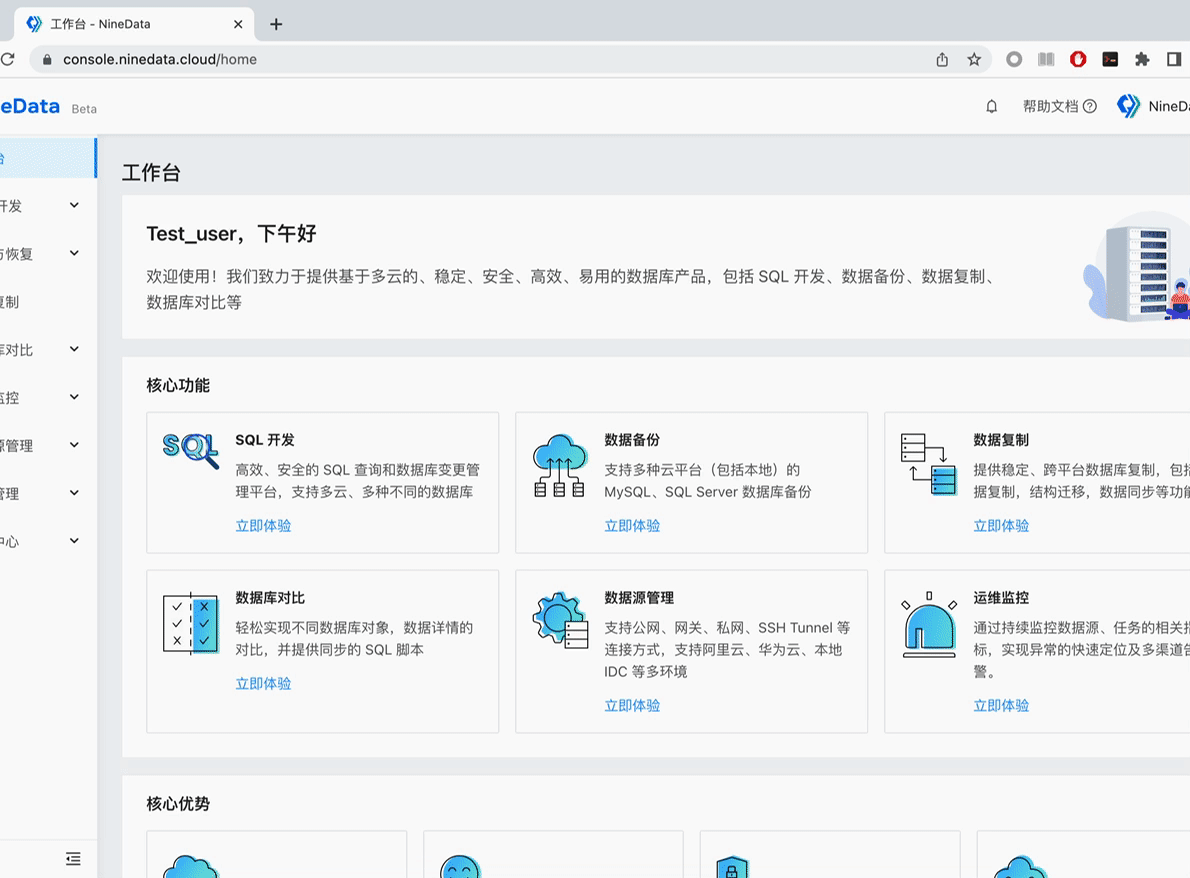
Visit the Org Login URL provided by the administrator in the browser, and the page will automatically jump to the KeyCloak login page.
Enter the username and password, and click Log In to jump to the NineData console.
 tip
tipThe username and password are the user information entered by the administrator in OpenLDAP, please refer to Add Organization and Users for the entry method.
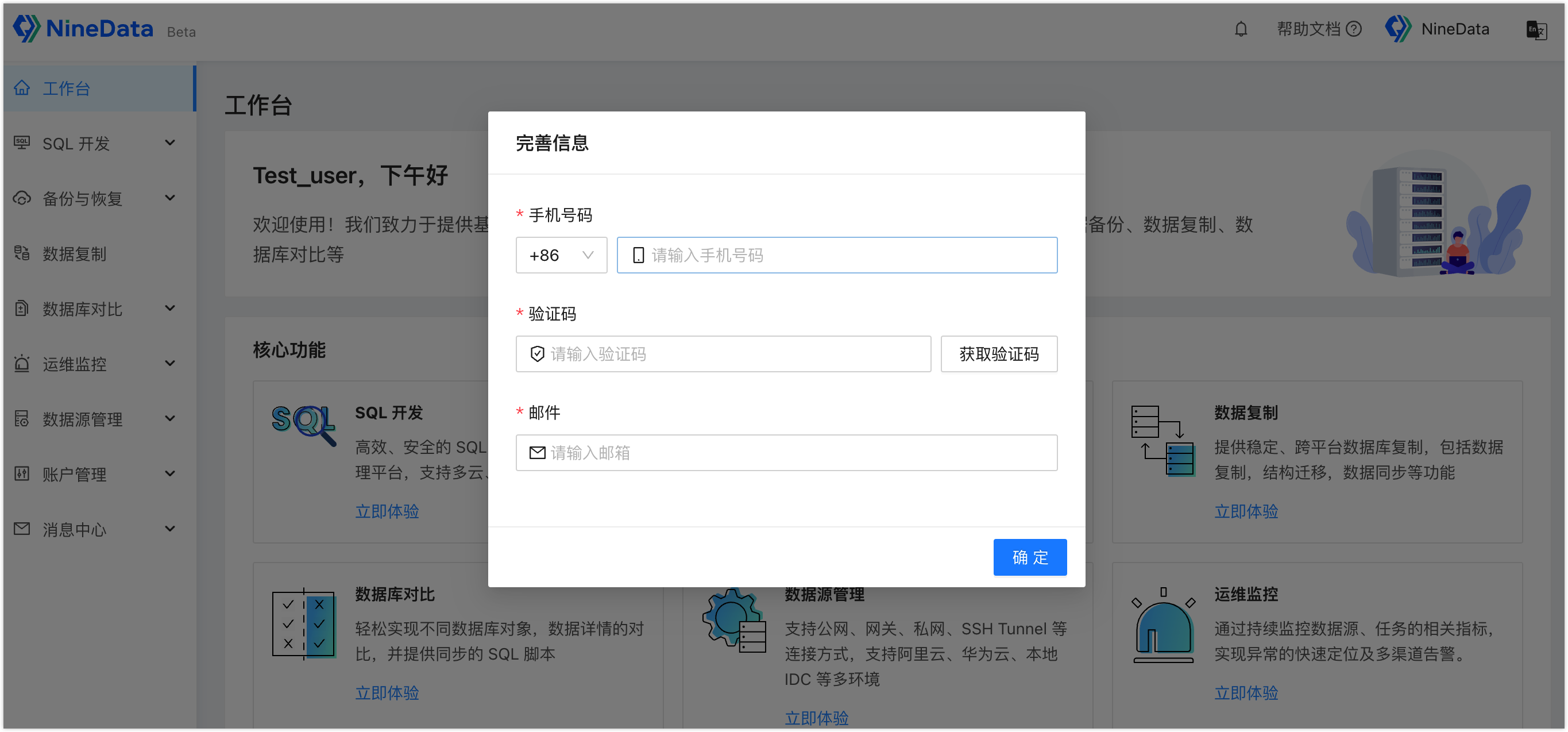
New users need to complete personal information according to the page prompts before they can continue to use.